While most consumers will only have one WAN (Internet) connection, there are times when two WAN connections may be better than one:
- Your primary internet is not stable and needs a backup internet connection.
- Your primary internet is slow and needs another line for bandwidth and redundancy.
Firewalla's Multi-WAN feature will help you manage a maximum of two WAN connections in either primary/failover or load balancing mode. Experiences inside a multiple-WAN network should be similar to a single-WAN network, if not a bit better, with the added availability and bandwidth.
- Multi-WAN Setups
- How to configure Multi-WAN
- Additional Multi-WAN Configurations
- WAN Connectivity Test
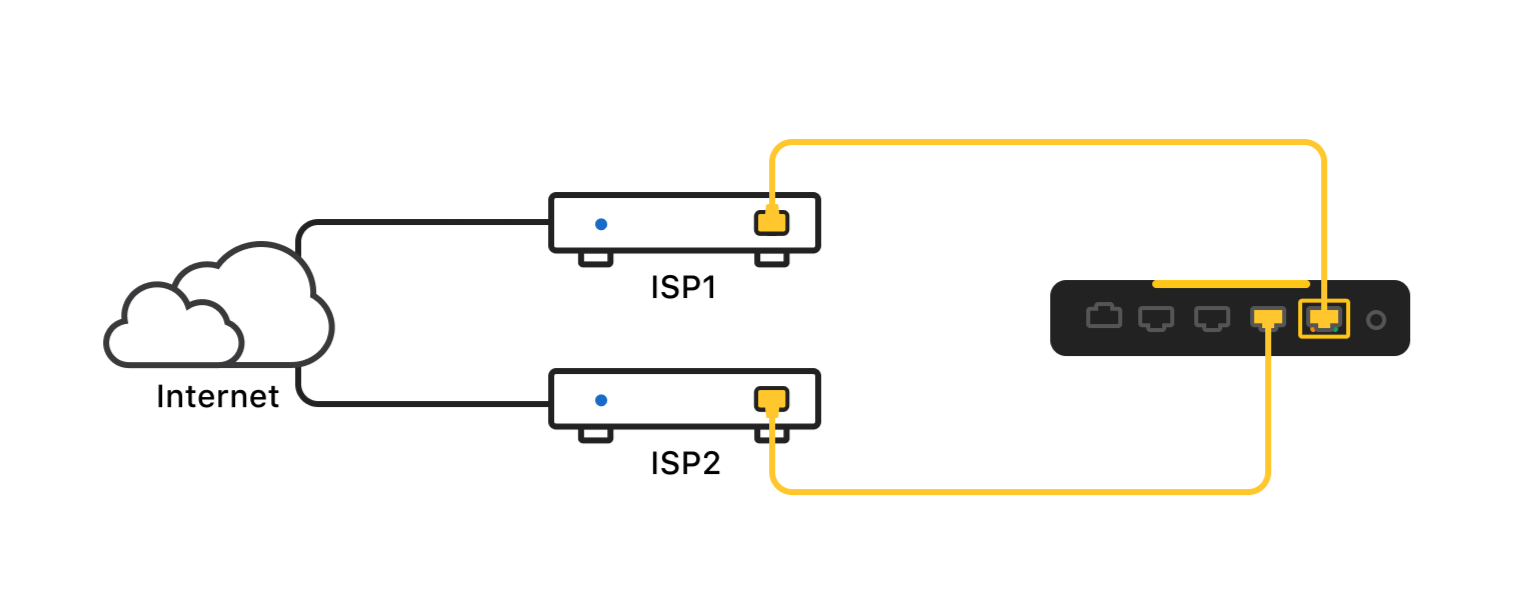
Multi-WAN Setups
If you have Firewalla Gold:
You can use one of Gold's ports as a new WAN interface, just like your primary WAN, or get a Wi-Fi SD and back up your home network with Wi-Fi.
If you have Firewalla Gold + Firewalla WiFi SD:
The Firewalla WiFi SD can be used in conjunction with the Firewalla Gold (and future Gold products) to enable you to tether to your phone (or another WiFi hotspot) when your main network is down and have the Firewalla Multi-WAN support automatically swap your primary internet (and automatically swap back once your primary internet is up).
See Firewalla WiFi SD tutorial
If you are using Firewalla Purple or Firewalla Orange:
Firewalla Purple and Firewalla Orange allow a maximum of one Wi-Fi and one Ethernet WAN connection for a total of two WAN connections.
Purple and Orange Wi-Fi WAN can tether to your mobile phone and create a dynamic backup internet for your whole house while the primary WAN is down.

If you have a Firewalla Purple SE, you can use the Firewalla WiFi-SD to create a WiFi-WAN for failover.
If you have a multi-WAN configuration, Firewalla will show you the live throughput on each WAN separately when you are connected to the local networks.
How to configure Multi-WAN
Multi-WAN configuration only becomes available when more than one WAN network is enabled, and your box is running in "Router Mode". Currently, Multi-WAN settings only support 2 WAN connections.
To create a new WAN connection:
- Tap on Network Manager
- Tap on Edit -> Create Network
- Select WAN Connection
- Tap the Ethernet Port or the Wi-Fi interface you'd like to create the WAN connection on, then save your configuration.
After you create a secondary WAN, you can configure how multiple connections handle Internet traffic under "Multi-WAN Setting". There are two modes:
- Failover (Default)
- Load Balance
Failover (Default)
Failover mode is intended to ensure the availability of the Internet connection, where you can use a standby network to take over when the active connection fails. In this case, only one WAN circuit is active at any time. There may be traffic on the standby to do basic connectivity checks.
- Active & Standby State: When both connections are enabled, the Primary WAN will be active, and the other one will be on standby. If the active connection fails, the standby network will become active to maintain uninterrupted internet connectivity.
- Primary WAN: The Primary WAN will be active when both connections are available at the same time.
- Auto Failback: When the primary connection fails, the standby WAN takes over. If Auto Failback is enabled, the connection will fail back to the Primary automatically when it resumes.
If you are using DDNS or VPN with failover mode:
- DDNS always points to the Active WAN.
- Traffic on the VPN Server network will always be sent to the Active WAN. If the Active WAN is down, you'll need to manually re-connect the VPN.
- VPN client traffic will be sent to the primary WAN.
- All traffic will be routed to the Active WAN unless specified.
Policy-based Routing
If you want to "lock/pin" certain traffic to go to a certain WAN connection, you can create a "route" for it, so that when this WAN is down, the traffic matching the "route" will be dropped instead of going through the network on standby.
For example, if you are using your mobile hotspot as your backup WAN on Purple but you don't want video or gaming traffic to kill your mobile plan, you can create Routes to send all video and gaming traffic to the primary WAN connection and set the Route Preference to Static.
On the contrary, if you want to send your video traffic to your primary WAN only when it's available, and allow the traffic to go through to the secondary WAN when the primary is down, you can set the Route Preference to Preferred.
More details on Firewalla Policy & Content-based routing.
Wi-Fi Calling
Another example is wi-fi calling. If you have trouble with Wi-Fi calling in a multi-WAN configuration in Load balancing mode, it may be because traffic is split between the WANs, and incoming packets may come over a different WAN than the corresponding outgoing traffic went over. The solution is to create a Preferred Route to send the required ports and domains for Wi-Fi calling over one WAN. For example, for Verizon, you can create routes for:
- Ports: 500,4500
- Domain(s): wo.vzwwo.com
You can find a few other carrier settings here or check with your mobile carrier. With preferred routes for these in place:
- All Wi-Fi calling traffic will go over the specified WAN as long as the WAN is available, but if not, traffic will failover to the alternate WAN. Wi-Fi calling traffic won't be load-balanced.
- All other traffic will be load-balanced according to the settings you selected.
Example Routes look like:
.
Load Balancing
Load balancing distributes network traffic across multiple networks. It helps improve the responsiveness of internet access and ensures no single network gets overloaded. This mode is ideal if you live in areas that have slow and unstable Internet.
Weight Ratio: Load balance allows you to set a relative weight for each WAN connection. The weight is defined as the percentage of traffic (or connections) sent through the WAN.
- If one of the WAN connections fails, the other will take over all the traffic.
- Load balancing is done at layer 3 or by looking at the IP address. If all your flows have the same destination IP address, they will always flow to the same interface. This behavior is to ensure that your network works correctly when dealing with banks and other services that check the source IP.
- Load balancing may not work for sites (like banks) that check the consistency of the source IP address. If this happens, you can manually route traffic to stay on one network using Firewalla Policy & Content-based routing.
- DDNS will be pointed to a random WAN.
- Traffic on the VPN Server network will be sent to a random WAN.
- VPN Client traffic will be distributed between the two WANs.
- All traffic will be distributed between the two WANs unless specified.
Additional Multi-WAN Configurations
Internet Speed and Quality Testing
You can test the Internet Speed and Quality of your WAN networks separately. Tap the Network Performance widget at the top of your box's main page, then scroll down to the Internet Speed and Internet Quality sections. Tap on Test Options in the top right corner of each section to set up automatic testing. You can set different server preferences, Internet bandwidths, and test settings for each WAN.
If you have Internet Speed testing set up for both WANs, you'll see two speed charts displayed on your box's main page.
To run the speed test manually, just tap Test Internet Speed and select which WAN to test.
Adaptive Smart Queue
Smart Queue Adaptive Mode auto-prioritizes traffic based on your Internet speed. You can set different speeds for each WAN, so Smart Queue Adaptive mode can better adjust its policy based on which WAN traffic is going through.
You'll be asked to enter Internet speed information when creating a WAN or turning on Adaptive Smart Queue (Adaptive Smart Queue can be turned on directly from the Smart Queue page or through the auto-configuration wizard). Internet speed will also be used as a reference for your Internet speed test results.
Monthly Data Plan
If you have a monthly data cap from your ISP, Firewalla's Monthly Data Plan feature can help you track your data usage.
Tap the Data Usage button at the bottom of your box's main screen; you'll see monthly and daily data usage charts for each WAN. You can enable the Monthly Data Plan and set different data usage limits, reset dates, and alarm settings per WAN.
Once enabled on multiple WANs, you'll see separate widgets on your box's main screen, so you can easily view your data usage at a glance.
WAN Connectivity Test
WAN Connectivity tests are used to decide which WAN circuit can be used and to trigger failover and fallback actions if necessary. There are two types of tests available for each WAN connection: Ping Tests and DNS Tests. If one of the tests fails, the WAN connection will be considered lost.
Ping Test:
- Up to 3 Ping test targets are supported.
- You can edit the Ping Test Count and Success Rate Threshold.
The test will ping each target several times (Ping Test Count) on every test. If the success rate is lower than the Success Rate Threshold you've set, the test will be considered as failed.
DNS Test:
You can edit which domain is used for the test. If DNS servers fail to resolve the target domain, the DNS test will be considered as failed.
Learn more about Network Events and Connectivity Test.
FAQ
Why am I seeing activities on my standby WAN?
There are some scenarios in which traffic will go to the standby WAN:
- Internet Quality Test is enabled on the standby WAN.
- WAN Connectivity Test is enabled on the standby WAN.
- Internet Speed Test is enabled on the standby WAN.
- Policy-based routing rule routes traffic to the standby WAN.
- IPv6 is enabled on the LAN, while the standby WAN supports IPv6 only.
- DDNS is set to the standby WAN, and VPN Server is enabled.
- VPN connection (VPN Client) was created when the primary WAN was down.
Comments
22 comments
When setup in Multi-WAN mode, it is possible to route certain devices out the ISP2 connection while all other devices route out the ISP1 connection?
Maybe a dumb WAN Connectivity Test question.
Since it was on by default after setup, should I assume it should be left on at all times?
Thanks
@nozero, do you see the tests are off?
@Firewalla,
No, still on.
Advanced Options
Connectivity Test
On
>
Test Targets
To test Internet connectivity via Ping test and DNS test. If one of the test fails, the connectivity will be considered to be lost.
@nozero, Yes, we'd suggest you leave it on. The connectivity test is an important feature that can help you identify your ISP connection issues. More information here: https://help.firewalla.com/hc/en-us/articles/4405487405587
@Support Team, Great, and thanks for the info link!
I love that this exists now, but I do have a question.
I have a use case where I would like to hook up my mobile hotspot as backup(WAN2), but if the primary WAN1 goes down and uses the mobile hot spot (WAN2), I only want to allow ONE device (work laptop) to be able to utilize the internet on that backup (WAN2) vs the entire house. Would that be easy to set up, assuming I would just create a RULE that blocks all from that WAN2 then allow only the one device?
The best way is to turn off the obvious bandwidth hogs and leave the other devices on. There is absolutely no need to turn off everything, many IoT devices don't communicate that much, and if you turn them off, may lose functionalities
I have an issue where I have set up primary and secondary, and it all works really well. I love it, because it's actually come in handy a few times during WFH video calls. However, if my secondary gateway loses power, I lose ALL internet connectivity (my primary is still live, and if I connect directly to it, it isn't disconnected from its WAN). I found this out when I was moving my secondary to a new location a few feet away and had to power it down. I have since experimented and this is 100% replicable. I'm guessing this wouldn't be considered a feature?
Secondary WAN down should NOT impact primary WAN
Did you setup any "routes" to force traffic going to the standby? or uses a DNS server only the secondary ISP? if not, send an email to help@firewalla.com, and we can look inside;
Is the Purple really Multi-WAN if you can only have one connection at a time?
Purple can have an ethernet based WAN and a WiFi-based WAN for the purple.
So we have no 4G/5G/LTE signal in our house due to security mesh on the doors/windows etc. I have one ethernet cable running out to our verandah currently wired into a Unifi AP. Is it possible to retain the AP and splice in a 4G failover device such as this: https://www.netgear.com/au/home/mobile-wifi/lte-modems/lb2120/
using a POE switch at the verandah, or do I need to run a 2nd ethernet cable?
When using load balancing mode is there a way to limit the upload bandwidth of one of the connections? It gets throttled pretty hard at the ISP level and I was hoping limiting upload speed here would fix that issue but I can’t figure out how to do that.
How does the latency test work when using load balancing? How do I know what WAN is being used when a High Latency event is triggered? The event notification is not useful if I don't know which WAN is the problematic one.
I have Comcast & Starlink. Starlink data is unlimited from 11p to 7a. How can I set Comcast to be primary WAN from 7a to 11p and Starlink to be primary WAN from 11p to 7a?
@Darin Jensen - Great question! Hope someone can answer this.
I'm seriously considering buying the Gold Plus. It might be overkill for an RV, but I don't want anyone to be able to siphon any of what little bandwidth I get.
I'm sure the answer is in its name - are all of the firewall features available when using it in a multi-WAN configuration?
Does the firewalla have to handle routing when using WAN failover? Wondering if I can leave the routing on my Eero POE Gateway, and just have the firewalla decide Mediacom or T-Mobile.
I have a Firewalla Gold. Is using the sub interfaces on a trunk port supported for WAN connections? I maybe getting Starlinkg and I would like to trunk it through my switch network and connect it to a subinterface on a trunk port on the Firewalla.
Are you talking about using a single port and run both WAN and LAN over it? where WAN and LAN are on your switch?
Is there a way to separate monthly usage data based on specific WAN interface? Right now I think it is all combined.
Thinking of how to have the Purple failover between two Ethernet connections but it only has one WAN port. What if both connections first go to a managed switch, tagged for different vlan id's, and the trunk connects to the Purple? If this works, then there would be multiple WANs separated on the OSI layer 3, but each WAN will also need a layer 4 interface to get an unique ip address.
Please sign in to leave a comment.