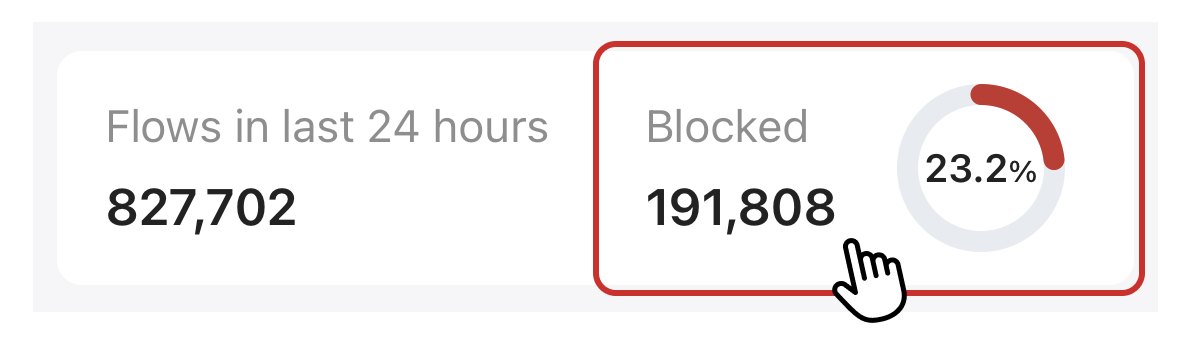
Interpreting Blocked Flows
Firewalla conveniently shows you all the flows blocked by your box. While this data is interesting, it's often misunderstood – for example, some people may assume high block statistics mean their network has been compromised, even though it could just be simple network scanning.
Here are some of the most-asked questions we get about blocked flows:
- What are blocked flows?
- Should I be worried if I see a lot of blocked flows?
- Why do I see known domains trying to access my network?
- How do I know which rule triggered a block?
- What do I do if I don't want this site blocked?
- How do I filter traffic in the Blocked Flows list?
What are blocked flows?
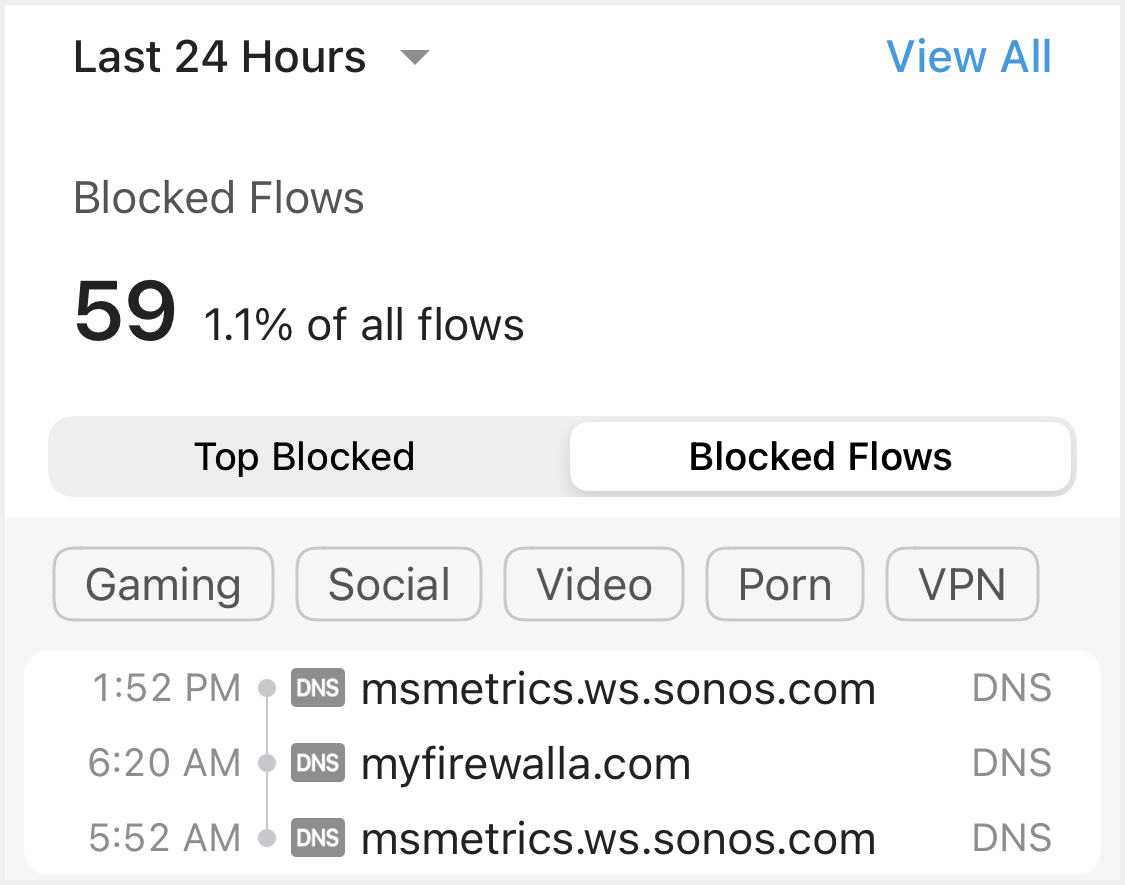
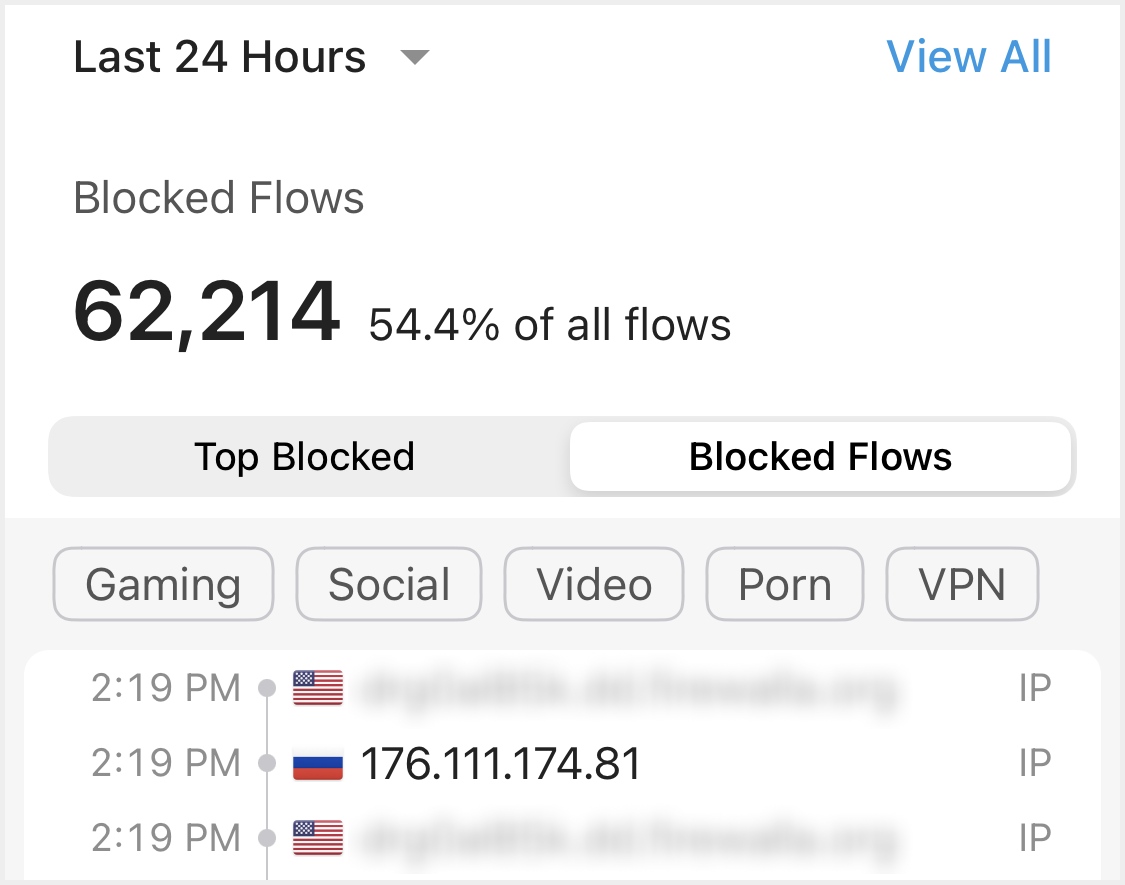
Blocked flows are flows intercepted by Firewalla. There are two types of blocked flows:
- Blocked by DNS Filtering
- Blocked by IP Filtering
Important blocks may also generate an alarm.
Most DNS blocks are caused by Ad Block or your other "domain" block rules, such as native family mode or application blocks, and some may be malware blocks. (DNS blocks may also include TLS blocks)
IP blocks are done in the data path, using an IP address. You will see many of these on your WAN interface (if you have a Gold or Purple unit). These blocks can be from any of your rules when you specify the default block mode. Not all IP flow blocks will show a domain.
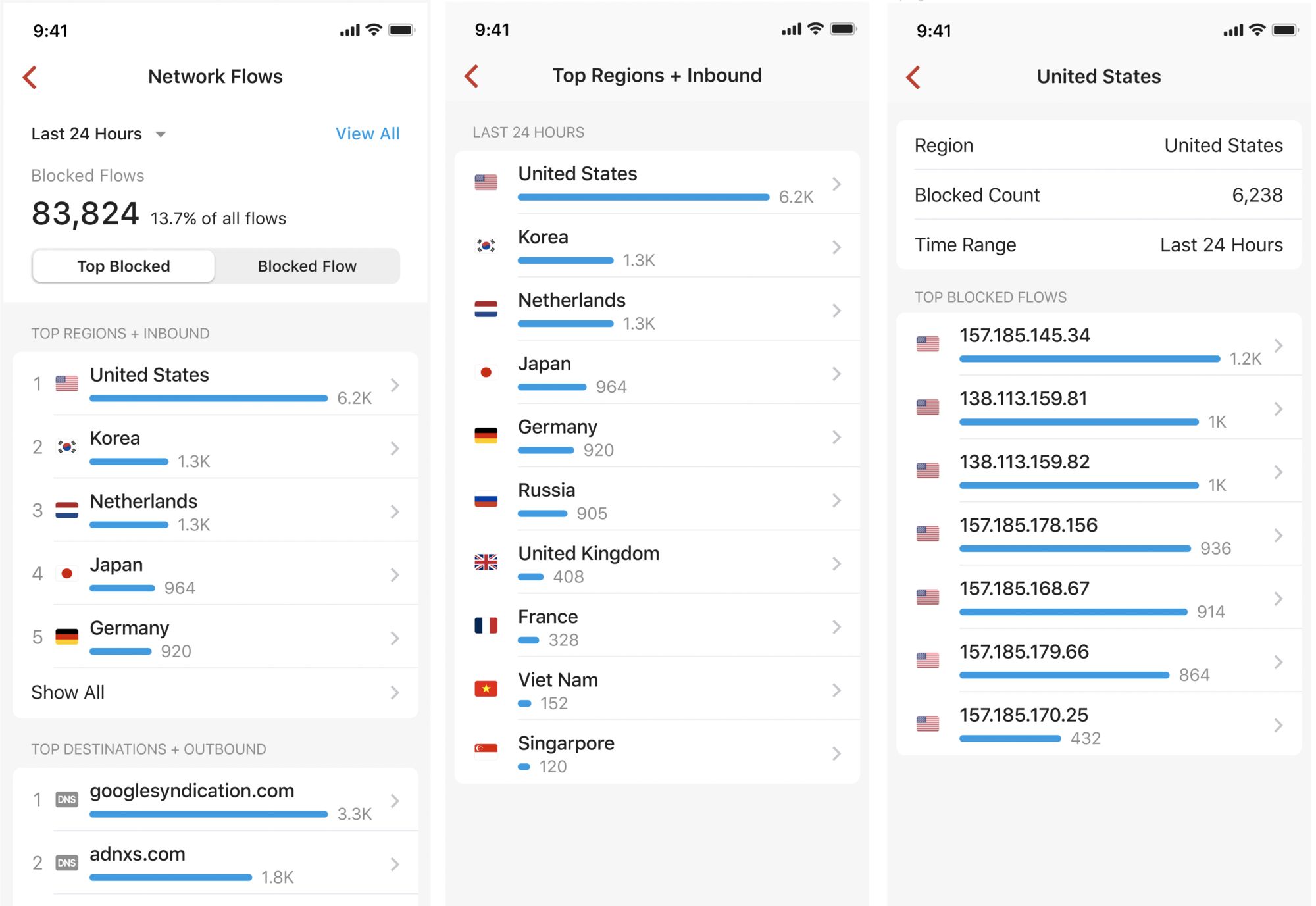
If you tap on Top Blocked at the top of the Blocked Flows page, you'll see a list of your Top Blocked Flows by Region and Destination.
- Top regions + inbound: your inbound blocked flows are aggregated by region so you can better understand which regions you should watch out for.
- Top destinations + outbound: your outbound blocked flows are aggregated by destination; most of them might be blocked by Ad Block or your own rules.
For step-by-step instructions on how to view this feature, watch our video tutorial.
Should I be worried if I see a lot of blocked flows?
Most of the time, there is no need for concern. When you are on the Internet, people may knock on your door– that doesn't mean they are allowed in. (Your Firewalla already blocked them)
Blocked flows can mean anything and depend on your devices, networks, the software you run, and your service provider, among other things. As long as your websites, apps, and network are running normally and you have Firewalla's ingress firewall on (Rules -> All Devices -> Block Traffic from the Internet), you should be okay.
If you think you're getting hacked, please seek help from an IT professional.
Why do I see known domains trying to access my network?
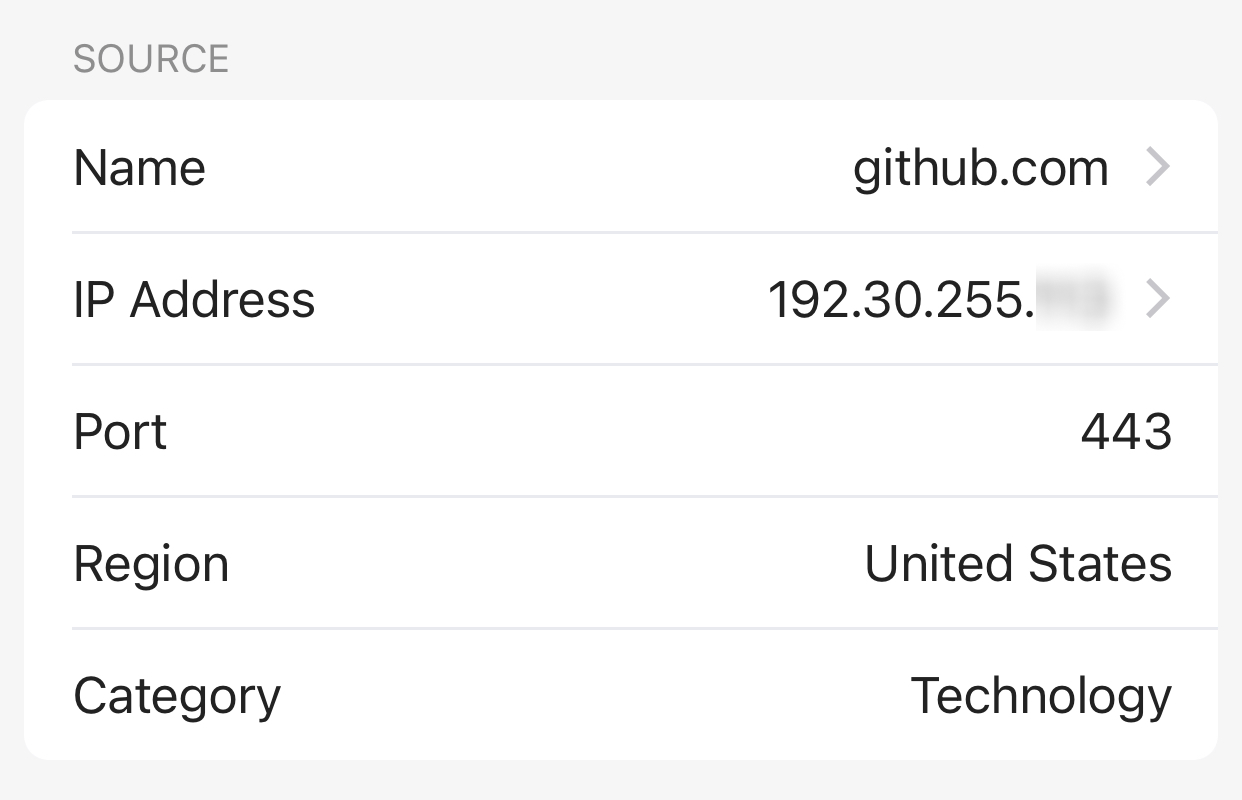
This is most likely the result of packets arriving after a session initiated by you was terminated. To learn more, tap on the flow. In the example below, the source of the flow was github.com and the port was 443. This is the port usually used as the destination.
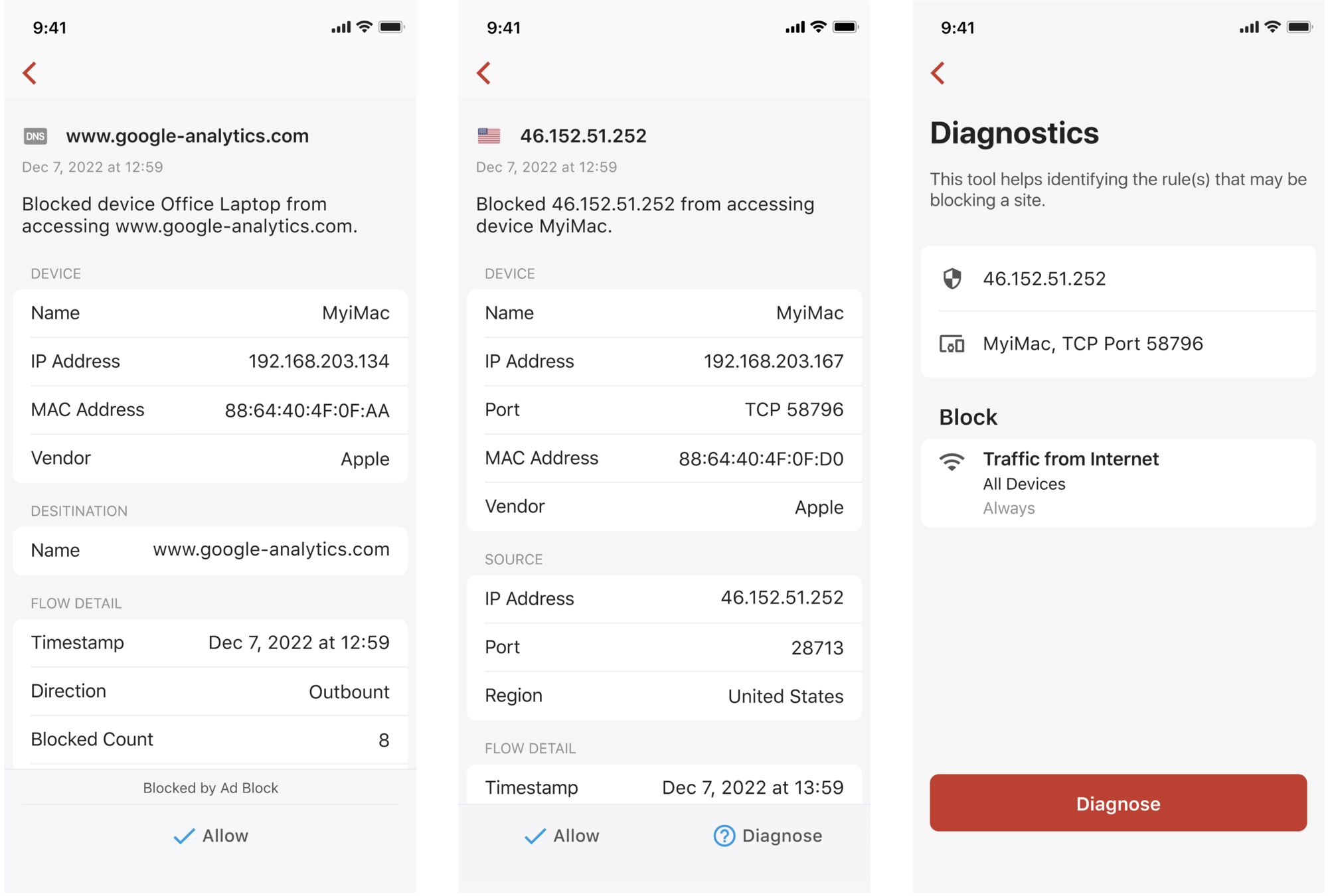
How do I know which rule triggered a block?
When you tap on a blocked flow, you'll find the feature that caused the block at the bottom of the flow detail page (if the flow was blocked by Ad Block or Active Protect). Tap on the line of text on top of the action to configure the feature directly.
Otherwise, you'll find a Diagnose button at the bottom of the page. Tap the button to identify the rule that blocked the site.
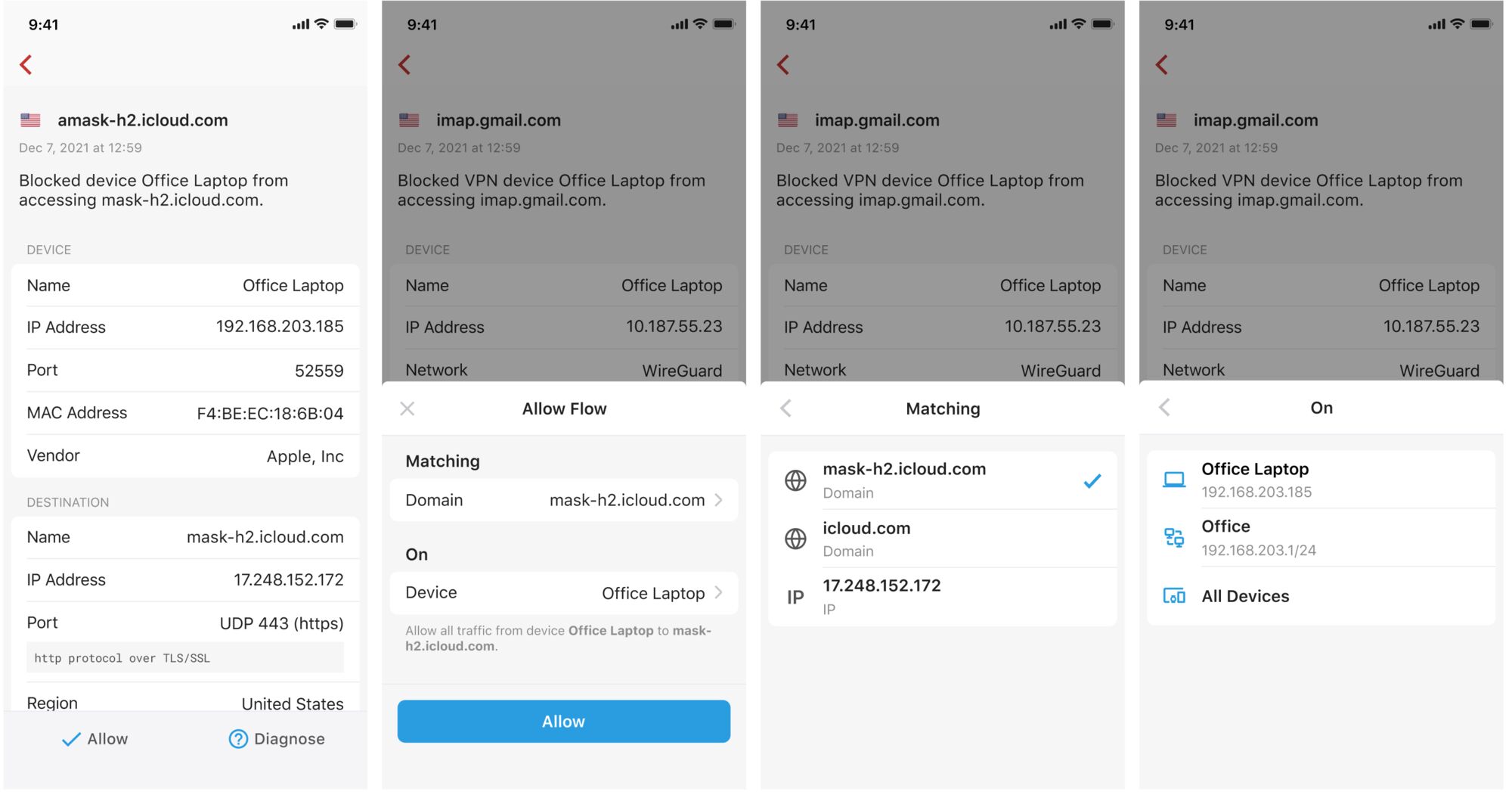
What do I do if I don't want this site to be blocked?
If you find that you don't have access to a certain piece of web content (e.g. an ad), look in your Blocked Flows list for a domain similar to the content you're trying to see. If Firewalla's blocking it, you can tap the Allow button at the bottom of the flow detail page to create an allow rule based on the destination/source and the scope of the flow.
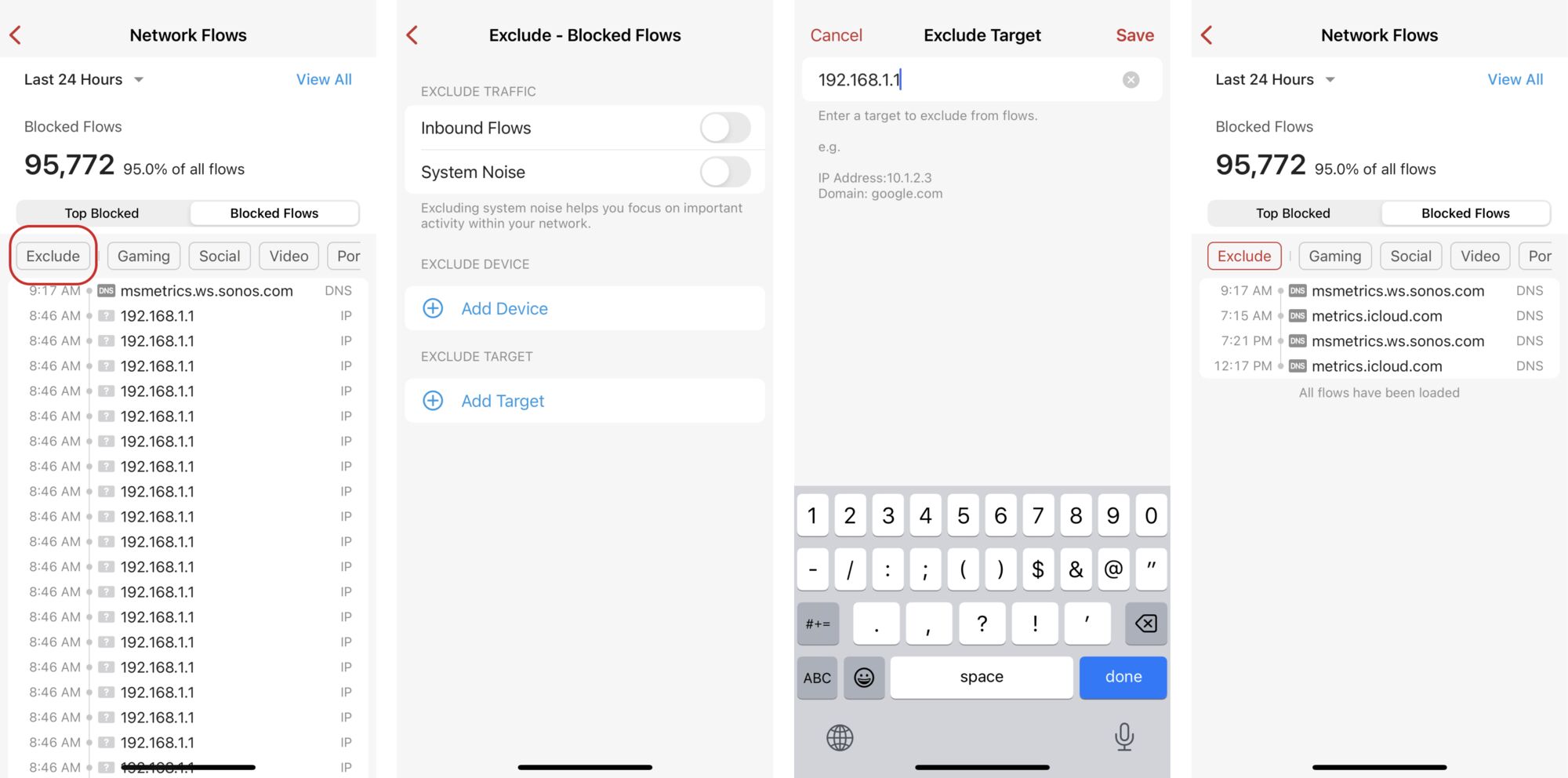
How do I filter traffic in the Blocked Flows list?
If your Blocked Flows list is filled with repetitive or unimportant flows, you can use our new Exclude option to filter out certain types of traffic. This feature is part of the 1.56 app release and is currently only available to early access users with box version 1.977 or above.
Tap on Exclude from your Blocked Flows list. You can choose to exclude inbound flows, system noise, traffic from a specific device, and/or traffic to a specific target.
This is part of our Firewalla Weekly Newsletter. You can sign up here https://firewalla.com/weekly.
Comments
0 comments
Article is closed for comments.