New Features:
1. Multiple WAN Failover/ Load Balancing (Gold)
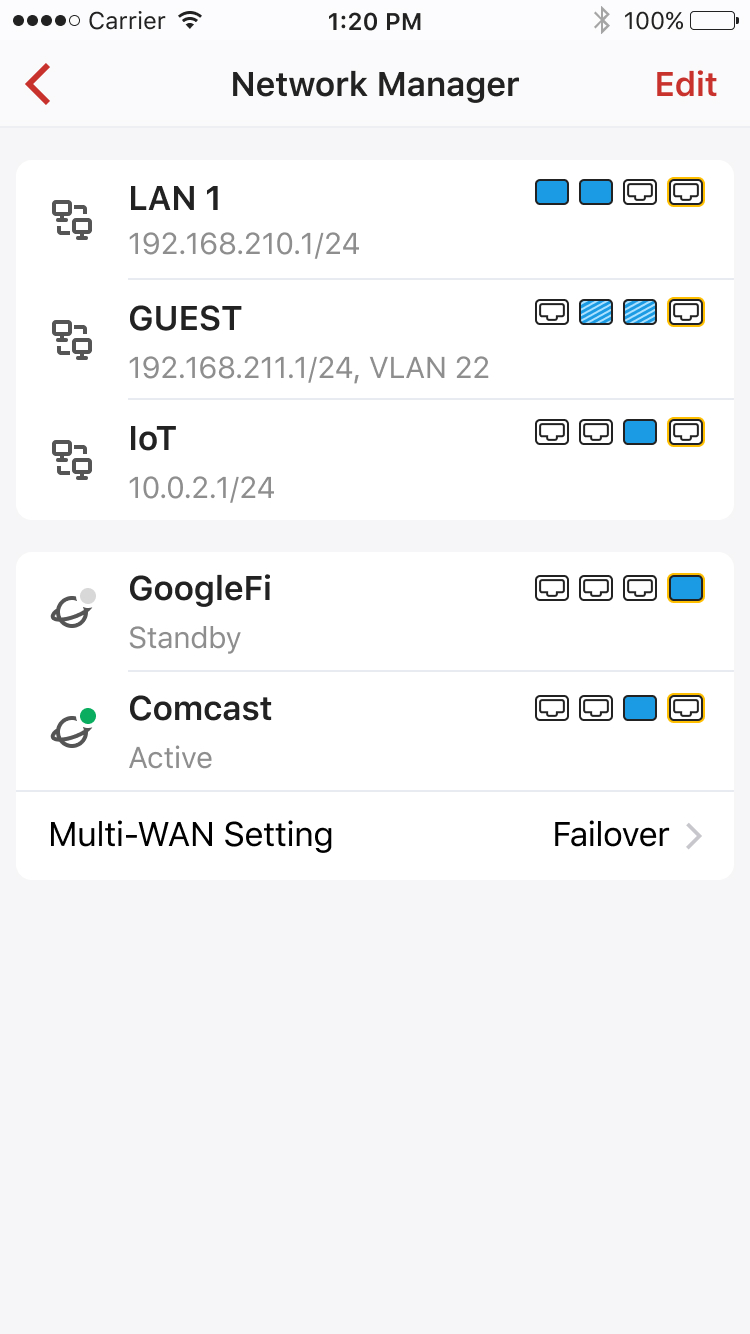
Multi-WAN configuration only becomes available when more than one WAN network is enabled.
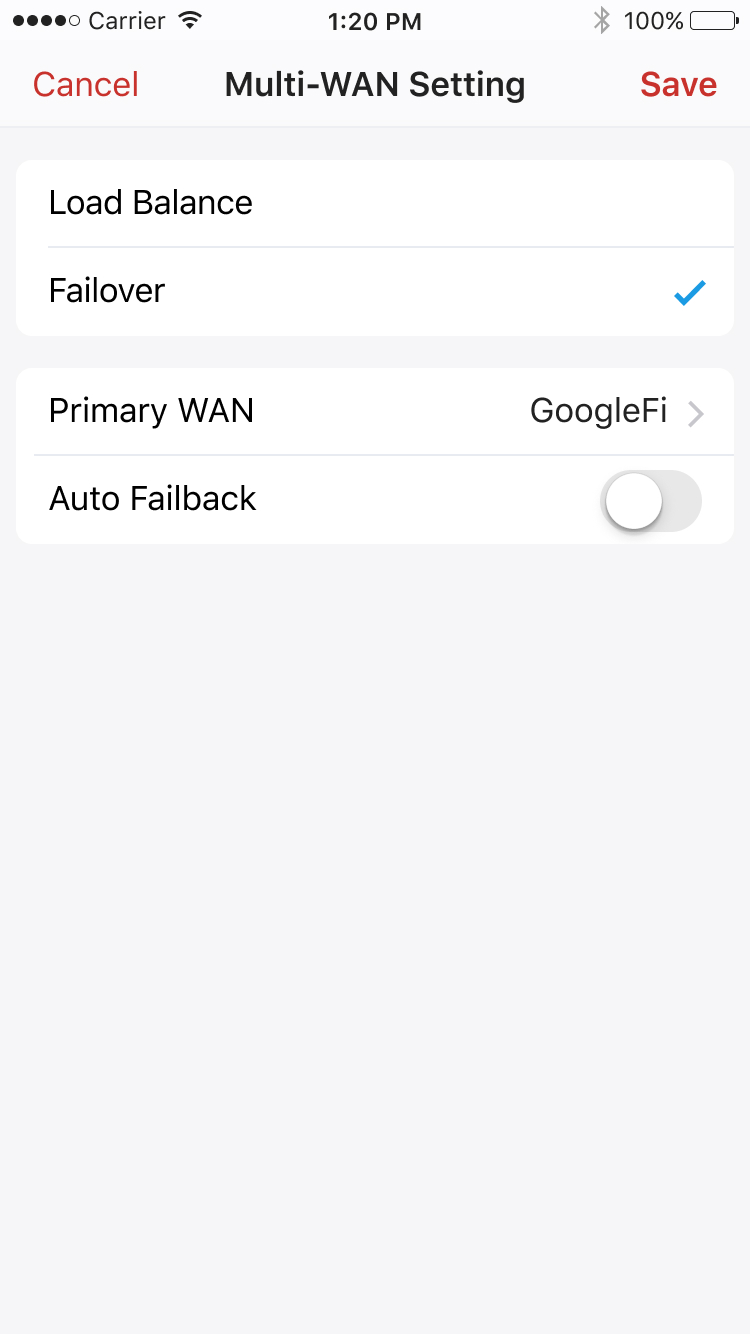
You can configure how multiple connections handle internet traffic. There are two modes:
Failover: Failover is intended to ensure internet availability, where you can use a standby connection to take over when the active connection fails.
Load Balance: Load balancing distributes network traffic across multiple WAN connections. It helps improve the responsiveness of internet access and ensure no single network gets overloaded.
The number of WAN connections is limited to 2 on the Firewalla App.
Learn more about Multi-WAN Setting
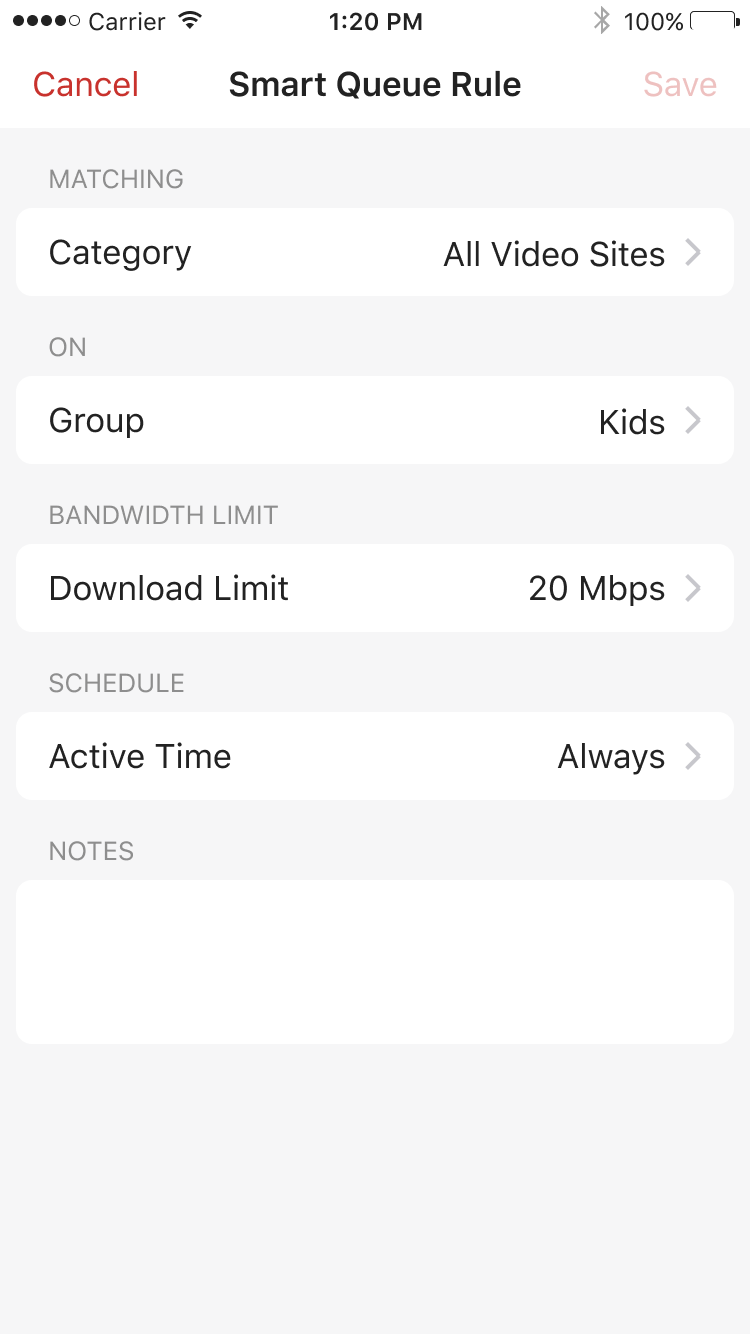
2. Smart Queue and Rate Limit (Gold)
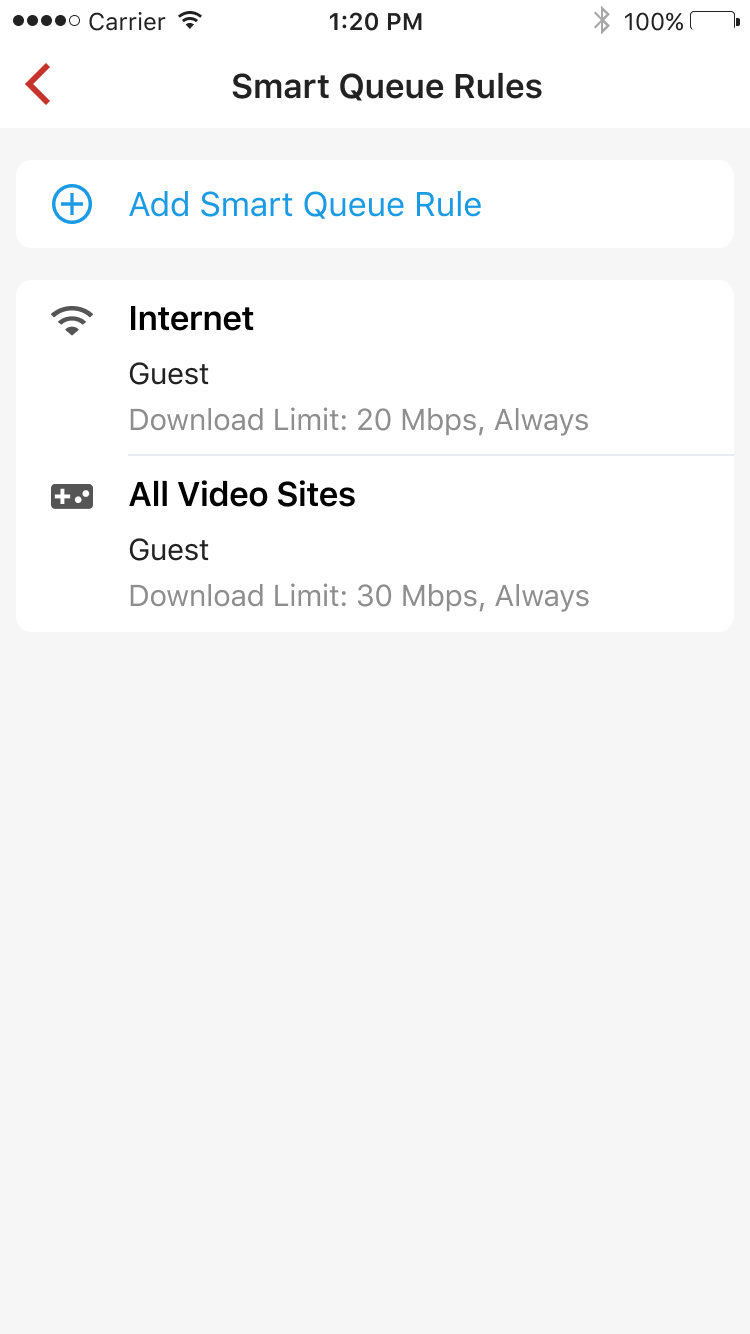
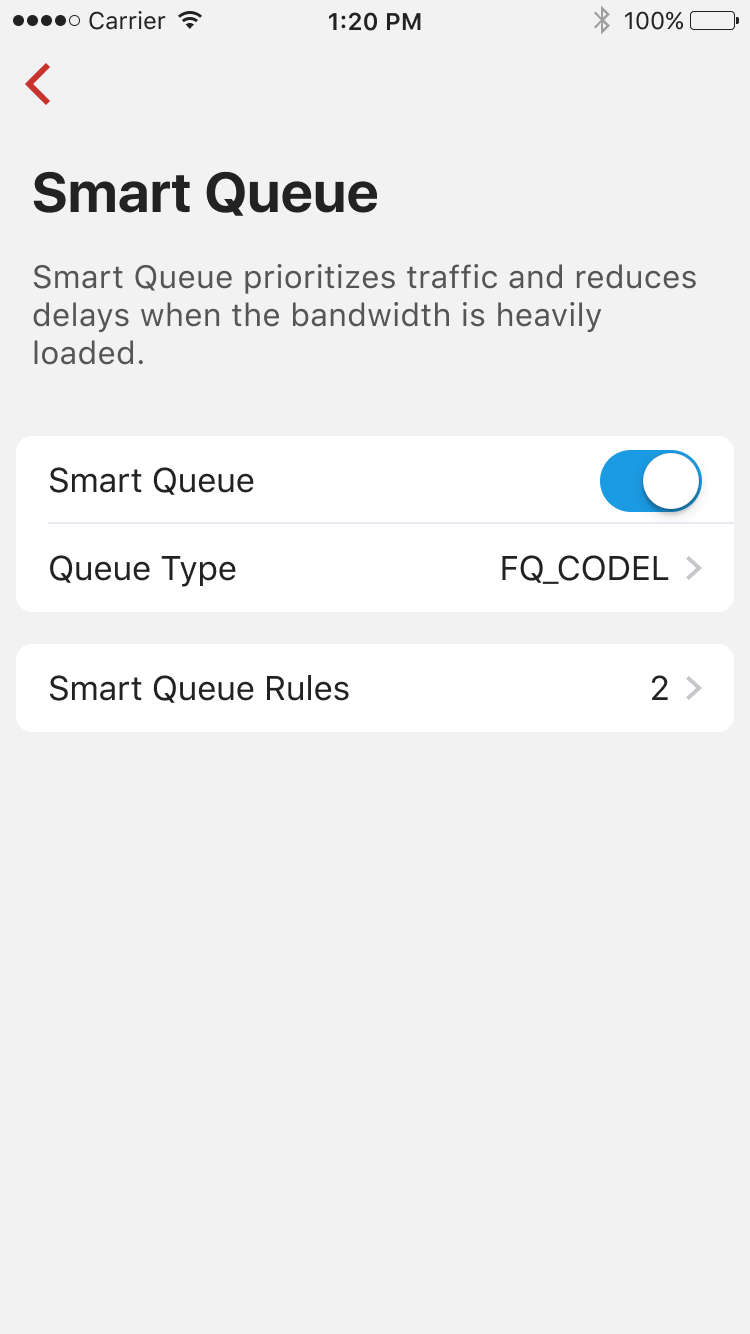
Smart Queue prioritizes traffic and reduces delays when the bandwidth is heavily loaded. By default, we use FQ_Codel to increase utilization across the entire network and manage queues with minimum delay.
You can create smart queue rules to limit the maximum bandwidth matching traffics on any specific device/group/network.
To change the default queue type or prioritize certain traffic will be supported later.
This feature only works in router mode.

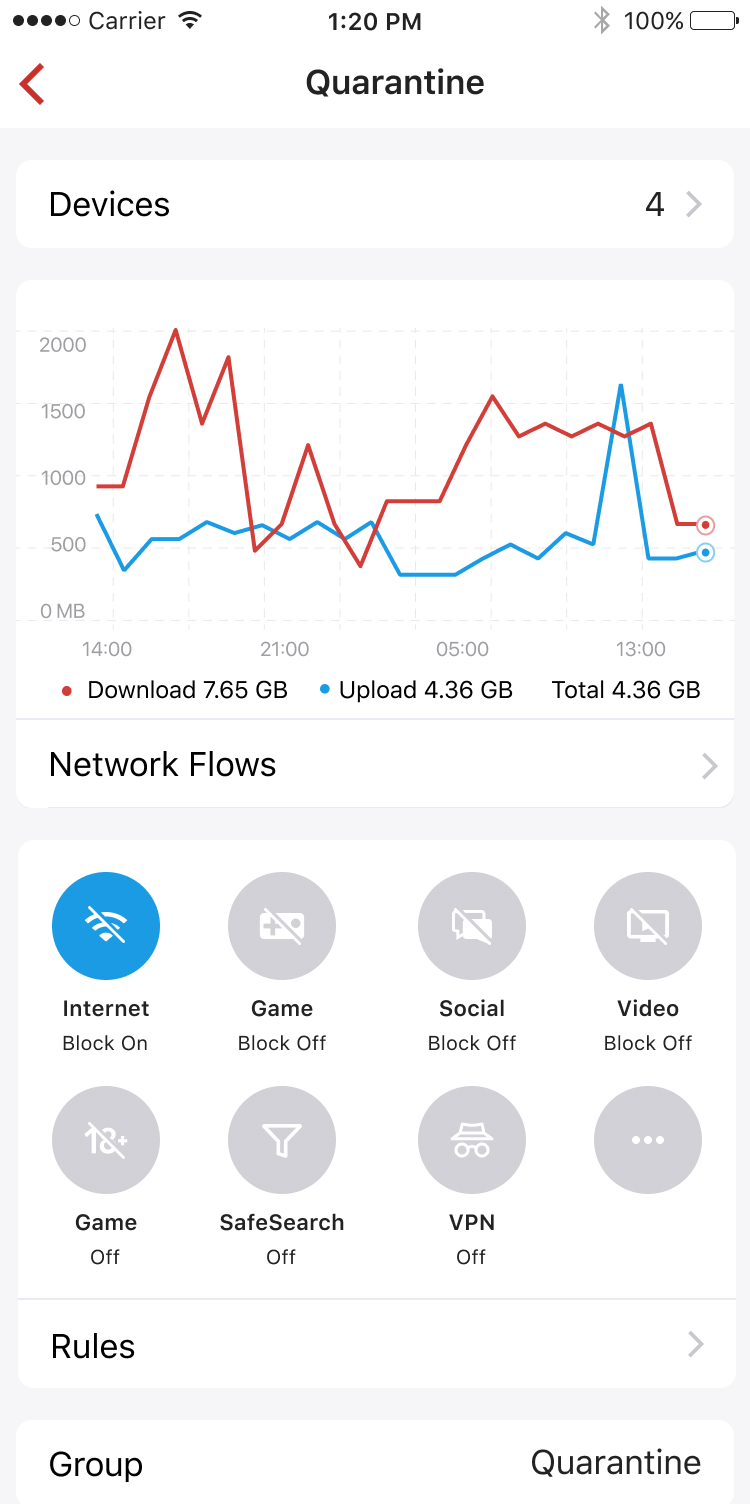
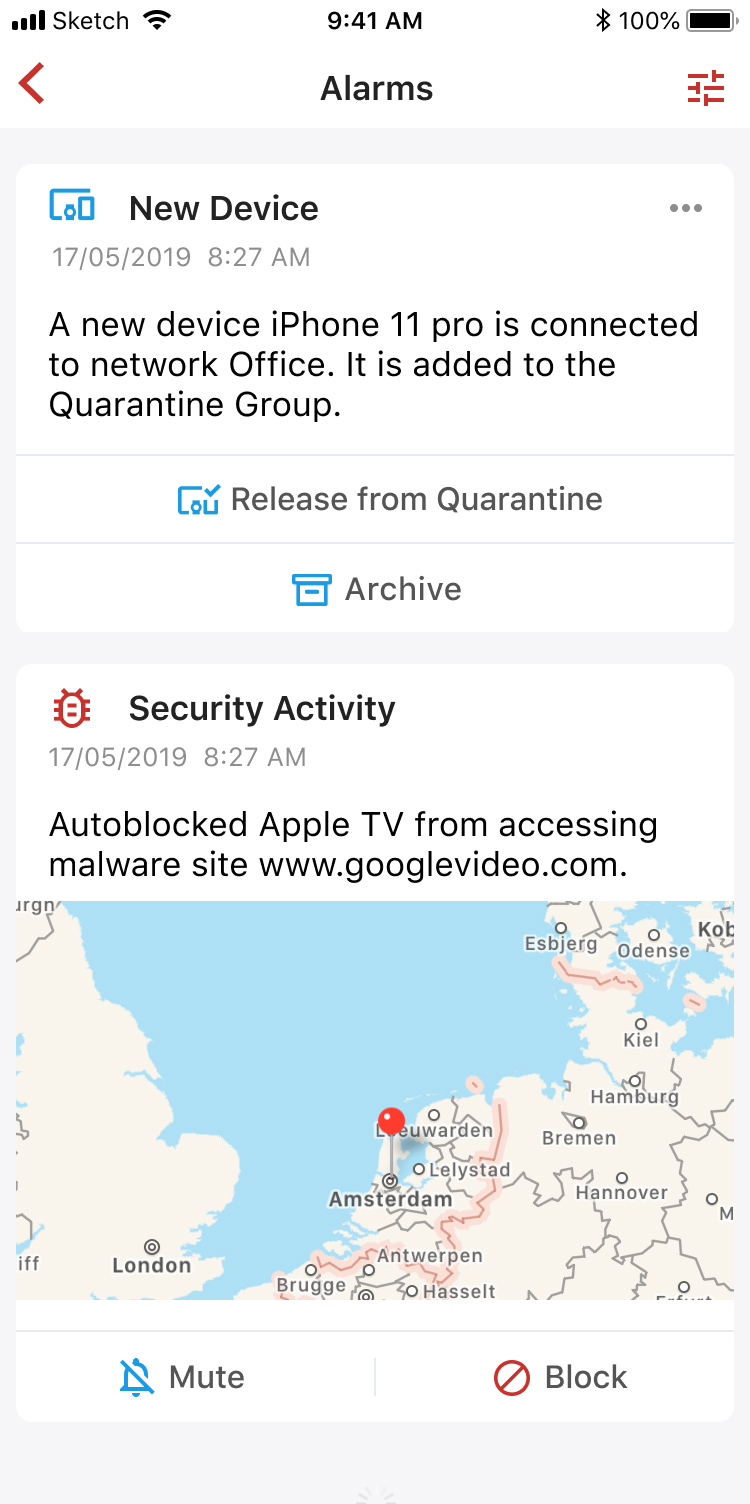
3. New Device Quarantine
New Device Quarantine creates a Quarantine group, with a set of pre-defined rules, to block new devices from accessing the internet and other segments of your network. The rules can be customized. When new device quarantine is enabled, new devices connected to your network will be automatically added to the quarantine group, and an alarm will be generated. You can choose to release the device from quarantine if it is trusted.
The quarantine group can be used as a simple guest network with very flexible rules.
To enable: tap on the "+" button on the main screen, and turn on "New Device Quarantine"
Learn more about New Device Quarantine
4. Customized Scripting and Docker (Gold, Blue+)
Custom hooks to safely execute user programs and scripts when Firewalla is rebooted. The scripts must be created under:
/home/pi/.firewalla/config/post_main.d
More details on this feature https://help.firewalla.com/hc/en-us/articles/360054056754
Please see this https://help.firewalla.com/hc/en-us/articles/360051625034 for a pi-hole docker example.
Improvements:
1. Support changing the port and protocol used for Firewalla VPN Server
2. Support creating networks with a template (Gold)
Improvements and bug fixes:
- <Null>
Known Issues:
- Issue: If you are using a Multi-WAN load balancing mode, a very small number of sites that check for a single source IP address may fail.
How to Fix: Policy Based Routing (1.972 release) - Issue: If you turned off UPNP under Port Forwarding settings, the existing ports opened by UPnP will not disappear in the open port list immediately.
How to Fix: The Ports are in fact closed when you turn off UPnP. The issue of not refreshing immediately is fixed in the 1.972 release. - Issue: IPv6 DHCP may not work.
How to Fix: This bug is fixed and will be released to beta soon - Issue: UPnP may not work on certain local networks if the subnet mask length is not 24.
How to Fix: This bug is fixed in the 1.972 release

Comments
27 comments
I am waiting for beta release. I don't want to mess up the box. Is there a page keeping track the bug progress? When do you think it'll be released to beta channel?
How do you enable "device quarantine"? It is not clear from this article and I cannot seem to find the switch in the alpha software on ios.
Do I need to have the firewallla gold in router mode to be able to use smart queue or rate limit? I can't see the option or menu in the app. I have the firewalla gold in experimental simple mode, an have enabled early access.
You will need to be in router mode for smart queues + rate limit to work.
Really looking forward to this! Multi-WAN is going to be so nice to have. Right now I'm manually swapping ethernet uplink cables into and out of the Firewalla when we need to switch which ISP we're using. :D
As others have requested, can we get an ETA on when this will be generally available?
There are still a couple of bugs on the early access at the moment (10/9/2020), once those are fixed we will push it to beta
I have an issue with MULTI-WAN on Early access. right now there are 2 WAN connections. they are in load balanced. Connection A 70% and connection B 30%. I don't know why but the Firewalla is getting the DNS traffic from connection B. if connection B fails instead of rerouting the DNS requests through connection A. The whole network goes down because the firewalla is trying to send the DNS through connection B and it can't. Is there a workaround for this or should I use Failover until beta release??
@Angel, I have created a ticket for you, so we can follow up. Is the A/B DNS different? they are ISP DNS or public DNS like 1.1.1.1?
@Firewalla, if I change the connected devices to a public DNS like 1.1.1.1 or 8.8.8.8 it works but I want to use the firewalla as DNS server because I think if I skip it maybe it could skip some blocking features. Do you block the websites and domains through DNS requests?. If not I can easily modify the DHCP to give 1.1.1.1 as Pref.
@Firewalla, I'm running Firewalla 1.971 in Advanced Simple Mode. It's working well so far, but today I got unusual alarms "newalarm.title.ALARM_DUAL_WAN". Network connections are likely working without any problem. Do you think this is kind of serious alert?
Hi Kaji,
That happened to me. You need to make sure you have the App with the latest update on your phone.
Greetings,
Hi Angel, Thanks for your comment! I didn't notice that new App version was released. I just updated to the App 1.40 on my iOS, and it seems going well.
Best regards,
Seems like Device Quarantine will be useful to discourage IOS user from re-enabling their Private Address to get around rules. But then again, this setup would not be compatible if have guests on your network.
I started playing with VPN Server and multi-WAN (load balance) on the same box (gold early access, 1.971). Looks like it is only using ISP 1 connection though for outbound traffic or and for the VPN server end point. Will it be possible to load balance connections to a VPN Server running on a Gold? If not, will VPN server and multi-wan at least work in failover mode?
@Bernie It is very likely the DDNS that is used by the VPN server to register its public IP address is mapped to the secondary WAN, which is a private IP address and not public routable unless there is port forwarding configured on the uplink router. If both WANs have public routable IP addresses, the VPN server should work no matter if it is failover or load balance.
@Firewalla, can we get another estimate on the Beta release date?
Device quarantine will be a very useful features, looking forward to receive the fw vers 1.971 in stable release channel;
I assume so, but I would like to ask and verify: will a new device, connecting to a vlan-tagging AP and arriving in the subnet of the vlan, also be auto-assigned to the quarantine group?
The device quarantine function applies to the whole network
@jeremya, we are extremely close ... could be any day now.
Hi @Firewalla, after the latest update with Early access. Suddenly the network stops and everything freezes and get super slow. There is internet access but the Firewalla semms to be overloaded or something. I can access the firewalla gold from outside and works fine but the monitor says there is no traffic. Also i stoppped the monitoring, Active protect, etc. and still same issue. After restarting the Firewall starts working but after 3 minutes back to where it was. Is there a way to go back to Beta or Stable???
Looks like 1.971 was released to Beta channel. My box was updated last night. No issue so far.
I can't seem to update to the beta from the current full release. Initially when I tried, it gave me a message about not having enough storage space. I went in and deleted the only thing I could think of, the DNS Cache. After that it allowed me to start updating to the 1.971 beta, but after 5 minutes or so it popped up a message saying it couldn't complete.
Is there more I need to do to prepare for updating to Beta?
SO MUCH AWESOMENESS HERE! I’m so excited!
Multiwan
Not ready yet for me to use it, but if you develop this further, I would love to see if it could replace my Peplink 305 that I use at work. https://www.peplink.com/products/balance-305/
The main thing with Multiwan that the Peplink device can do that Firewalla can’t has to do with the rules for load balancing. Specifically, on the Peplink you can have it load balance with Persistence. This makes it so that if a device starts a secure session with some destination, that traffic always goes out through one WAN connection. Critical for many secure web services. MANY of the cloud based services that we use at work will terminate the session if the traffic from a device changes from WAN1 to WAN2. the host figures you are connecting from two separate sites simultaneously and gets upset.
FWIW, i think Pepwave has implemented load balancing EXCEEDINGLY well and makes it really simple, so i think its worth your while to look at how they do it.
Smart Q:
This is cool! I’m playing with it now.
Quarantine:
Loving this! I’m wondering if this/along with device groups could possibly make setting up VLANs obsolete?
Can I use quarantine on devices that joins my main lan ...and those that are on Guest VLAN can continue getting access.
For users' general knowledge and understanding, can Firewalla devs comment on the subject discussed in the Community support section linked to below?
Your educational efforts added on top of functionality are part of what makes Firewalla awesome by the way.
Thanks!
"Firewalla Ubuntu 16.04 EOL"
https://help.firewalla.com/hc/en-us/community/posts/360052992553-Firewalla-Ubuntu-16-04-EOL
I just got updated to 1.971 (38902612).
Is that a new version?
This is a new version and it fixes compatibility issues with 1.972 (if you move from 1.972 to 1.971) We do this before 1.972 goes to beta :) so we are pretty close with another set of awesome features!
Please sign in to leave a comment.