This article has been retired and may contain information that is not up to date. For the latest information about how to build and manage network segments, please see our article on Building Network Segments.
Concept and Use Cases
Network Segmentation divides your network into physical or logical partitions with dynamic and static policies/rules. These subnetworks can be used to give you better security and in some cases help you to speed up the network. Network Segmentation is only available on the Firewalla Gold and Firewalla Purple.
Use cases for network segmentation include:
- Create a network segment for kids or employees with their own rules and policies. You can limit access to the internet, filter activities, and more.
- Isolate critical devices into their own network. For instance, only permit devices like security cameras to talk within their own network.
- Create a secure guest network, in order to apply high-level protection to your guests, and manage their activities in real-time.
Note: you will need a managed switch or AP that supports VLAN-SSID mapping to implement VLAN.
Example
We will demonstrate with an example of how you can use network segmentation and VLAN features in the Firewalla Gold to create a really powerful guest network. We will be using a TPLink EAP225 as the WiFi Access Point (Amazon $60). The EAP225 is also VLAN aware and can create a mapping between SSID and VLAN ID.
When this access point is connected to the Firewalla Gold, it will be running in bridge mode, leaving all layer 3 (IP layer/routing/filtering) functions to the Firewalla. This will conserve CPU on the Access Point to focus more to provide better wifi.
1. Configure a physical LAN
Connect the TP-Link AP to port 3 on Firewalla Gold, tap on the "Network Manager" button, and configure a 10.0.1.x network from the Firewalla app:
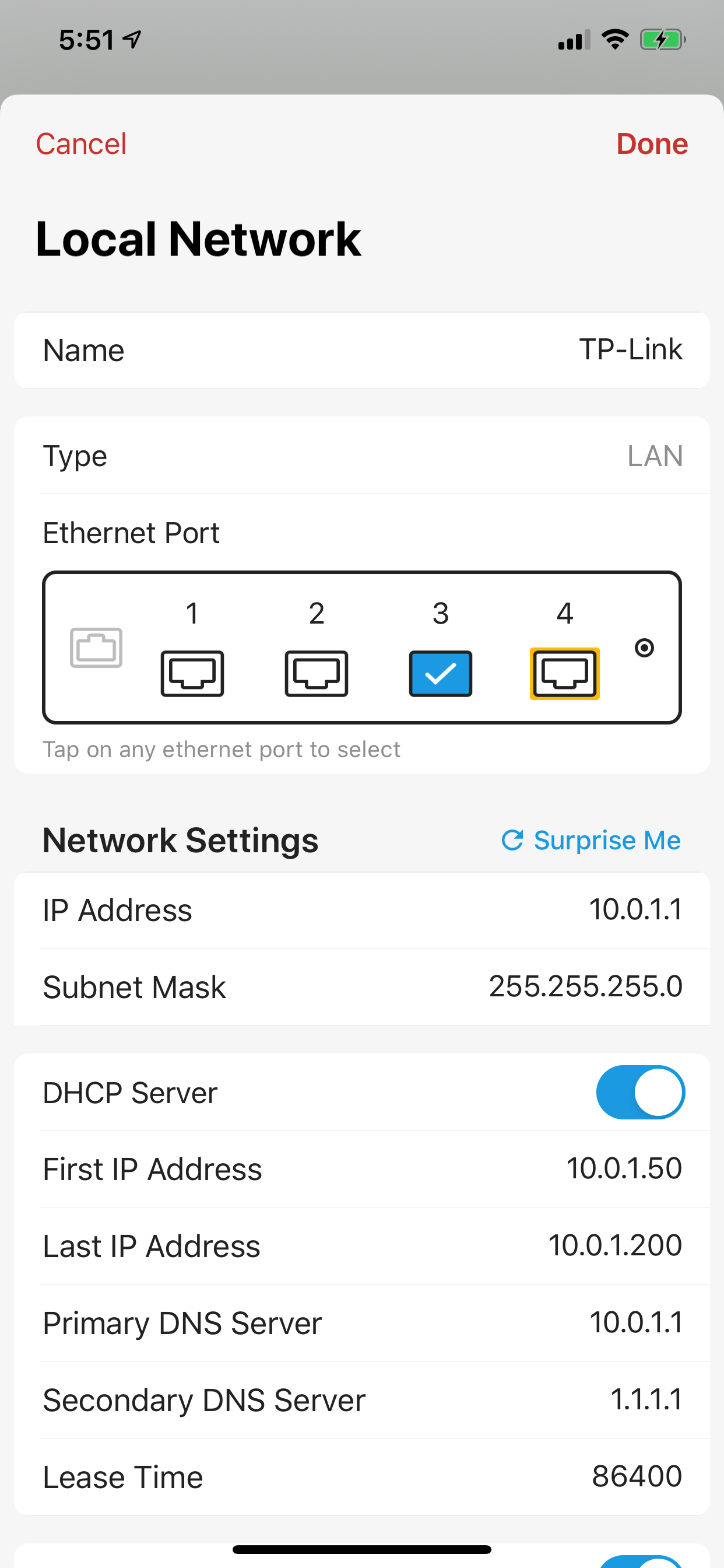
After configuration, make sure you tap on "save" to commit the changes to your router.
2. Create a VLAN
Here, we will configure a couple of VLAN's via SSID mapping in TPLink EAP225. Login to the TPLink AP and configure VLAN to SSID mappings as the following.
Note: Please use the IP address of assigned by Firewalla to log in to the Access Point. If you are using a router that has been configured into bridge mode or AP mode, the previous IP address of the router may not work.
Here the main network is mapped to VLAN 33 and the guest network is mapped to VLAN 44.
- VLAN 33: SSID TPLINK5
- VLAN 44: SSID TPLINK5-GUEST
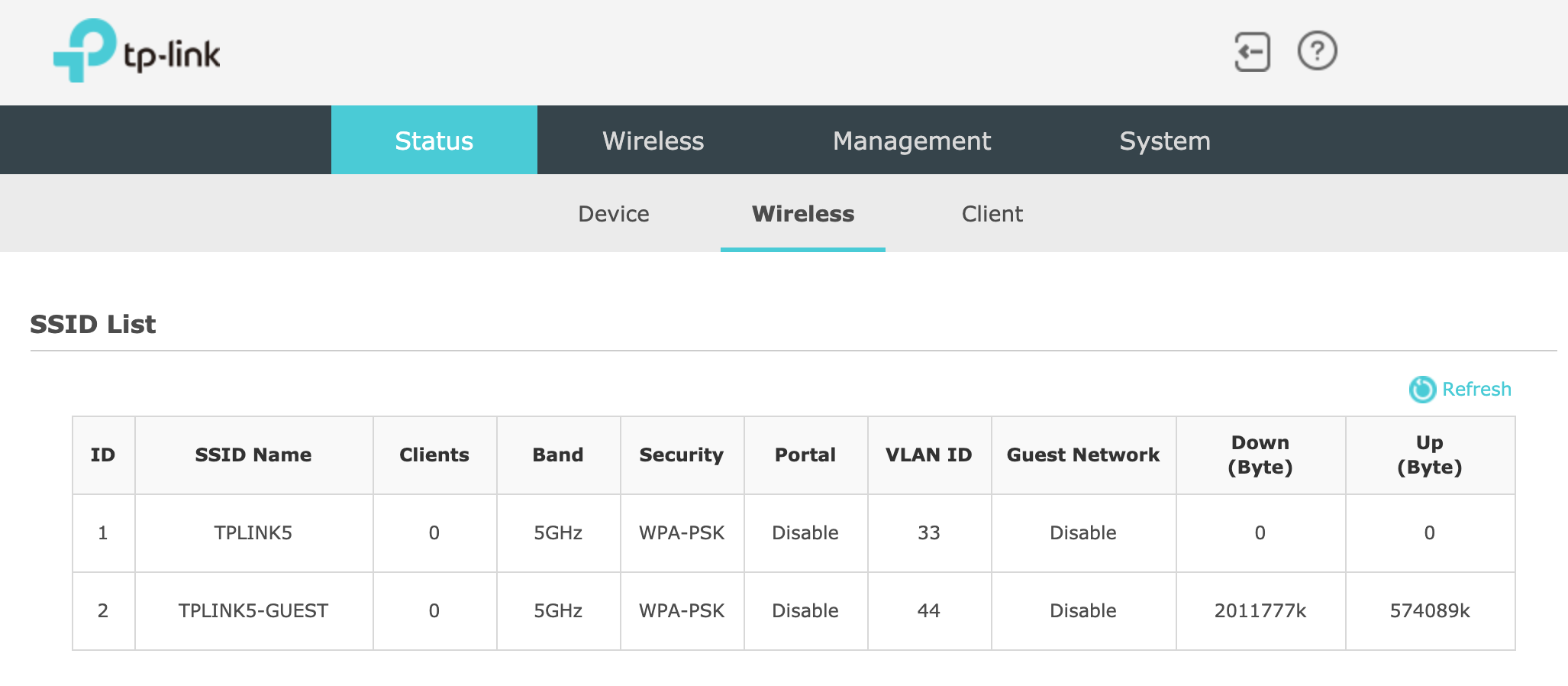
3. Create a guest network over VLAN
Now, let's go back to Firewalla App and tap on Network Manager. Using the Network Manager, we will create a VLAN 44 on port 3. (You can do the same for VLAN 33)
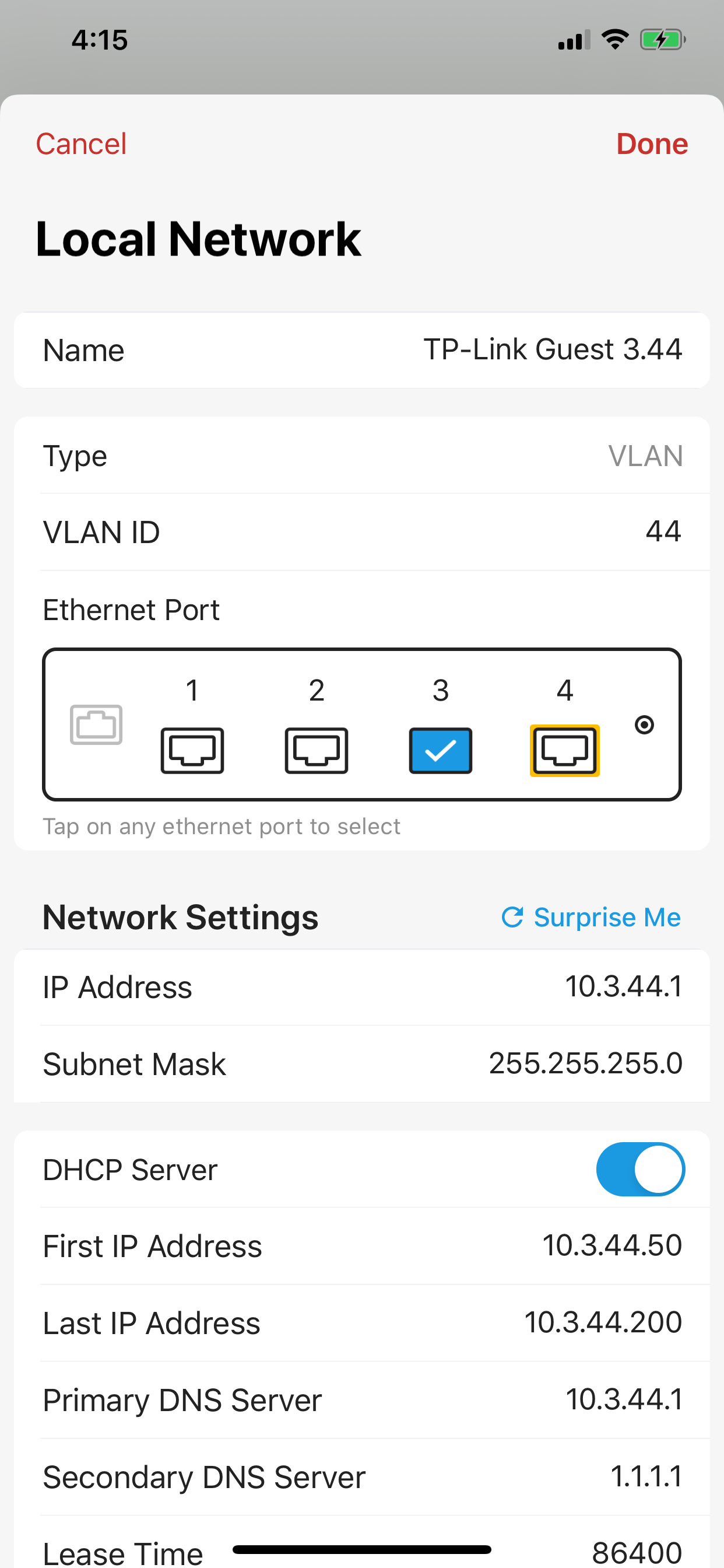
4. Apply policies to the guest network
After the guest network is created, you can apply features or rules just to this segment. For example, you can enable Family mode on the guest network. On the home screen, tap on Family Mode, and apply family mode only to TP-Link Guest 3.44.
Or you can tap on the rules button to create a rule like this one. Block the guest talking to any local networks ... but do allow devices from local networks to talk to devices inside the guest network.
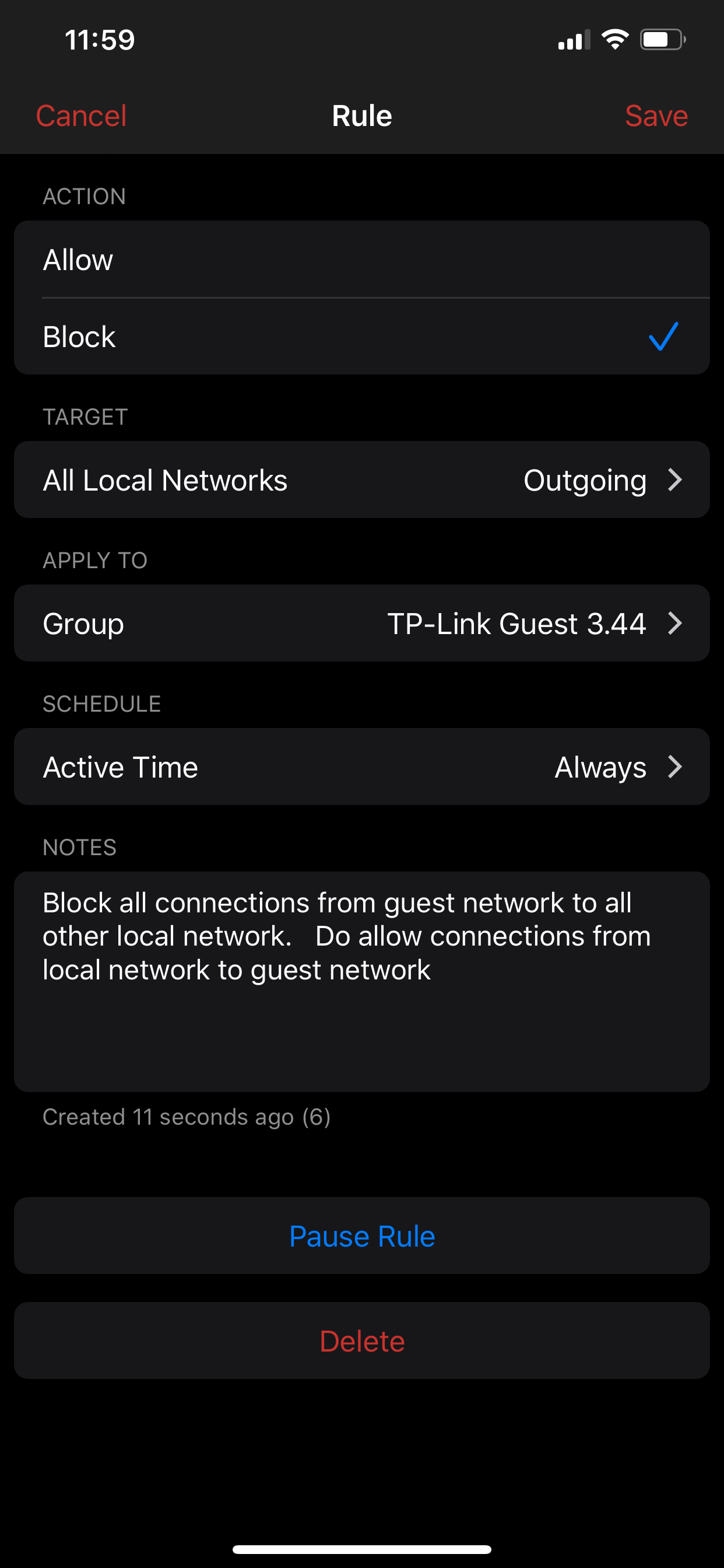
After all of the above setup is completed, you can simply join your device to TPLINK-Guest SSID and it will be put in the guest network TP-Link GUEST 3.44.
Comments
21 comments
I just picked up the TP-Link EAP225, which I am enjoying playing around with. There is one feature I'd really like to use but for the life of me, can figure it out. When I enable the VLAN in the EAP225 it locks me out of the admin interface and clients cannot connect to the device. The only way for me to get back in is to do a factory reset.
Setup - Step 1
VLAN - Step 2
Testing - Step 3
Any advice? Is there some sort of VLAN number convention I should be using instead of 33 or 44? I basically want to keep my IOT devices separated from my main LAN by using VLAN. In my Firewalla, I have a rule so that the EAP225 does not communicate with the main LAN, but if I could do it with the EAP as well, then I know this feature is working as intended.
Any advice?
Did you ever create a default VLAN (no VLAN ID) segment on port 2? Many of the managed switches uses the default to activate the management interface
I only created a new LAN on port 2 called 'TP-Link LAN', then two VLANs called 'IOT Data' with VLAN 33 and 'IOT Media' with VLAN 44. So I should create another VLAN with no VLAN ID?
I notice in the TP-Link EAP225 admin control panel there is a Management VLAN option. Should I enable that? If so, what VLAN ID should I use?
Sorry for my lack of VLAN technology, but is there something I need to do to trunk / tag port 2 on the FWG to the LAN / VLANs I created? If so, how?
@Rolando Nispiros
I’ll see if I can try to help you here…
I’m pretty sure you have a few options for a solution.
Need more info:
1.) What hardware version of the TP-Link EAP225 AP do you have? V3? (To make sure I’m looking at the right manual)
2.) Does your Firewalla Gold show that it has assigned an IP address to the AP? Does the FWG show that is has assigned the AP an IP address both both before and after you can no longer access the AP’s admin interface/GUI?
3.) How are you accessing its admin interface? By this I mean:
4.) Did you configure the AP to operate in “Standalone mode” as indicated in the manual?
5.) Is the AP’s DHCP server enabled or disabled?
There should be a few possible solutions, depending on:
I.) the design of the AP: if VLANs are created in the AP’s interface, does it still allow its admin management web interface on an untagged LAN? It seems from the tutorial on this webpage that the answer is yes. Otherwise, your only option is to enable Management VLAN (If you do this, a common recommendation is to change it from the universal default of VLAN ID 1 to something else for security). At first glance here, I think you can access it both with or without enabling a management VLAN.
II.) How you want to physically connect to it:
Thanks for taking the time to help. Really appreciate it. In regards to your questions:
1.) What hardware version of the TP-Link EAP225 AP do you have? V3? (To make sure I’m looking at the right manual)
Yes I have V3k with this build - V3_5.0.5 Build 20210604
2.) Does your Firewalla Gold show that it has assigned an IP address to the AP? Does the FWG show that is has assigned the AP an IP address both both before and after you can no longer access the AP’s admin interface/GUI?
Yes, the FWG does assign an IP address to the AP, which I use to log on to the admin web interface. After the enable the VLAN everything basically freezes/cannot logon to admin web interface anymore/refuses connections.
3.) How are you accessing its admin interface?
Via the IP address assigned by FWG - 192.168.181.96/index.html. But after I enable the VLANs to the SSIDs in the AP, the web interface freezes/locks me out.
I am not using an ethernet cable connected to the FWG to get to the AP. I am / was connecting to the AP via wireless.
As noted above, the AP is connected in Port 2 configured as a LAN in FWG. Also in Port 2 I configured 2 VLANs for the AP in FWG. Per the instructions here I created the VLANs in the AP, then created the VLANs in FWG. It's after this my connection is frozen/refused connection.
Is this the recommended sequence in your opinion? How do I tag/truck the FWG VLAN port to match the AP? I just don't see any other obvious mapping between the two devices or maybe I am supposed to use a specific naming convention other than the VLAN ID?
I did not check the box in the AP for Management VLAN. Maybe I should enable it, use a different VLAN number other than 1, then try again?
@Rolando
Here’s one possible solution:
If you are configuring your AP through a web browser and you are connecting to it directly over Wi-Fi, The simplest thing you should be able to do is:
Try this and let us know whether or not you are able to get it working this way.
In case you’re curious, Another method you should be able to do for additional security that is slightly more complicated is if you: enable the Management VLAN ID (change it from the default of 1 to anything else, like 22), create a management SSID exclusively for managing your AP, tag it with VLAN ID 22. You’ll first need to create this VLAN 22 and assign it to port 2 with a new corresponding IP range on your FWG (eg 192.168.22.1), and reserve the AP’s IP (or create a static IP in the AP’s admin interface) e.g . 192.168.22.101.
But try the simpler way first, and let us know.
Awesome, thank you for the tips, I will definitely give this a try after everyone is asleep or this weekend. Ah so that what it means for untagged traffic, sorry I'm such a VLAN noob. This new option gives me hope.
@Rolando
I forgot to mention you can try just enabling the Management VLAN ID and set it to be the same VLAN ID as you set on one of your two SSID’s that you assigned VLAN ID’s to, and manage your AP when connected to that SSID with your computer…but then everything else connected to that network e.g. on the ‘IOT Data’ network Will be able to see everything you’re doing while you’re configuring your AP, including what username and password you enter in order to login to it because the management interface is http and not https.
So a compromised IOT device automatically scanning for administrative traffic of networking devices can intercept all this, which is a risk I assumed you did not want to take.
For security I think it’s a lot better to have a separate network for administrating networking devices (Whether it’s for untagged traffic or if you create one with a dedicated VLAN and set the management VLAN ID for that) so that’s why I recommended you have a separate SSID for that purpose instead of simply enabling management VLAN for one of your IOT networks.
Understood, thank you. Yes I want to isolate IOT data, but will keep this in mind.
No worries! We all start learning somewhere :)
Yes for sure! I'm a learn as you go person.
@mobius strip - thank you for helping me and for the recommendations! It all worked. I think creating a separate SSID not on a VLAN / not tagged did the trick for me. I was able to get into the web admin console without any problems and I can see from the client list that the IOT devices have picked up their new IPs. Can't thank you enough!
@Rolando Nispiros
That’s great! I’m glad to know that you have a successfully working solution :)
Yes really enjoying me set up now, thank you!
Question - I just purchased FW Gold. I intend to use EAP-610 (TpLink) with VLAN tagging on the various SSID's I configure for my IoT devices. The 610 has PoE. I intend to connect the 610 to a TPLink PoE Switch (which supports vlan tagging as well), and connect that to the FW Gold.
Since the Gold seems to require port driven tagging, do I also need to tag the port that has the switch, or will the frames from the 610 automatically be recognized as their respective VLAN's and thereby segmented by the rules I create in the Gold? Any suggestions or guidance is greatly appreciated.
I created a few VLANs under LAN 1. How do I assign devices to that VLANs to practice micro-segmentation? For example, I have an entertainment VLAN and a PC VLAN - I do not want the nodes within those VLANs to communicate with each other.
Awesome, now to work out how to determine/set a blank with an Asus router in AP mode :)
Your comparison sheet shows a difference in the feature set between the Purple and the Gold. What will i miss here if I go to the Purple?
I have a gold. If I create a VLAN on port 3 can I configure it without a quarantine group? I have a multi tenant office space and setting up one office with groups, rules, and a quarantine to prevent access, but the other tenant will be open. I am separating them via separate switches, but using one modem and one firewall gold.
Please sign in to leave a comment.