App Release 1.48 is available on iOS / Android.
New Features:
- Custom time for pausing rules
- Scheduled emergency access (1.973 only)
- Kid Lock: unlock App using Face ID, Touch ID or PIN
- Ethernet Port Link Speed Display (1.973 only)
- Directional ALLOW Rules
- Wi-Fi Management (Purple only)
- Link Aggregation (Gold only)
- Multiple IP Addresses on WAN Interface
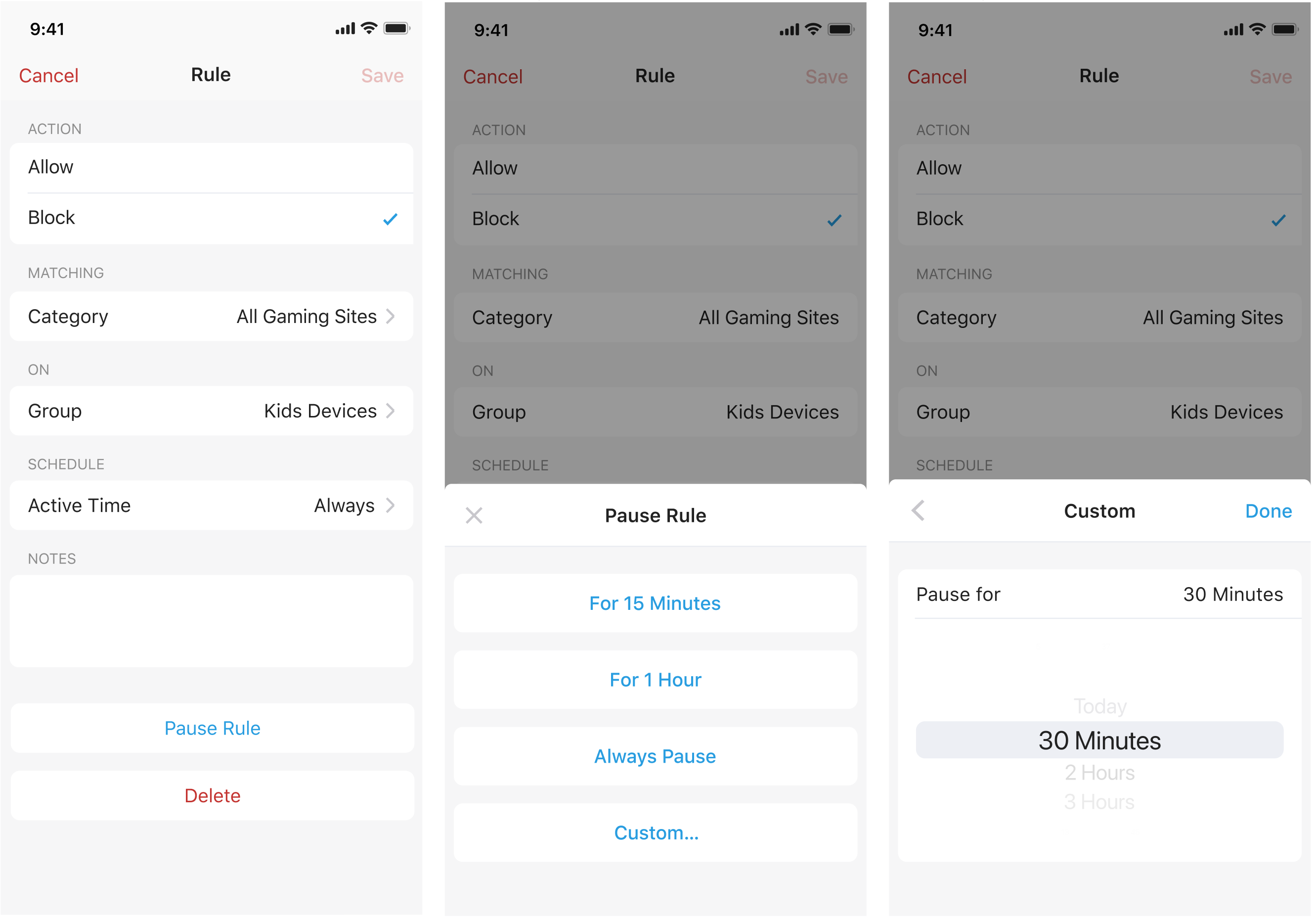
1. Custom time for pausing rules
You are now able to customize the duration when pausing rules. Just Tap Pause Rule -> select Custom… -> pick any duration -> tap Done.
A rule can also be paused for "Today", which means it will be paused until the end of the day.
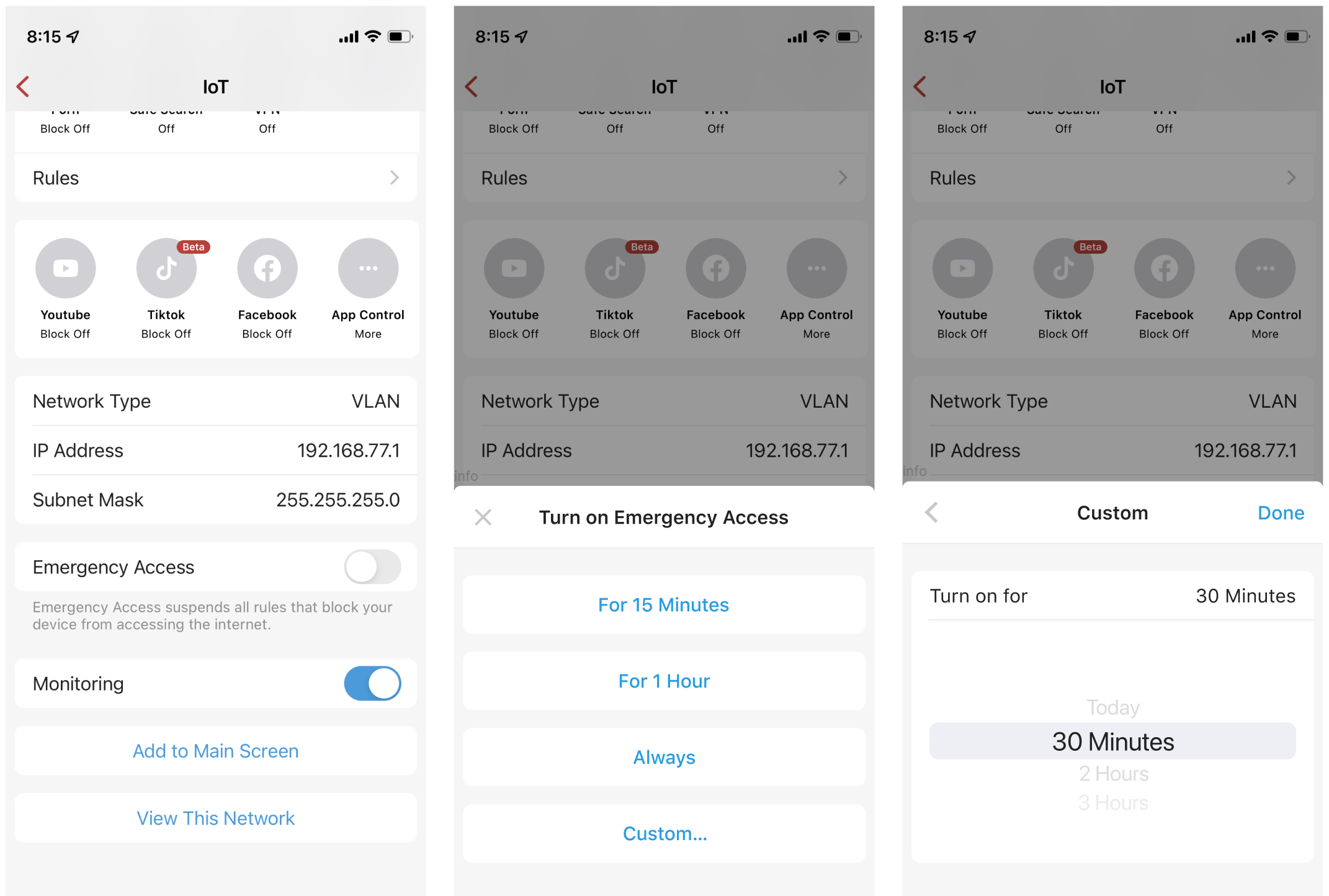
2. Scheduled emergency access (1.973 only)
Some of you use emergency access to give temporary access to sites; to make this process more secure, we are now providing you with the ability to schedule Emergency Access. Similar to pausing rules, emergency access can be turned on for 15 minutes, 1 hour, always, and more importantly, any custom time you'd prefer. At the end of the specified period, Emergency Access will automatically be turned back off. No more forgetting to turn off Emergency access.
Learn more on managing devices.
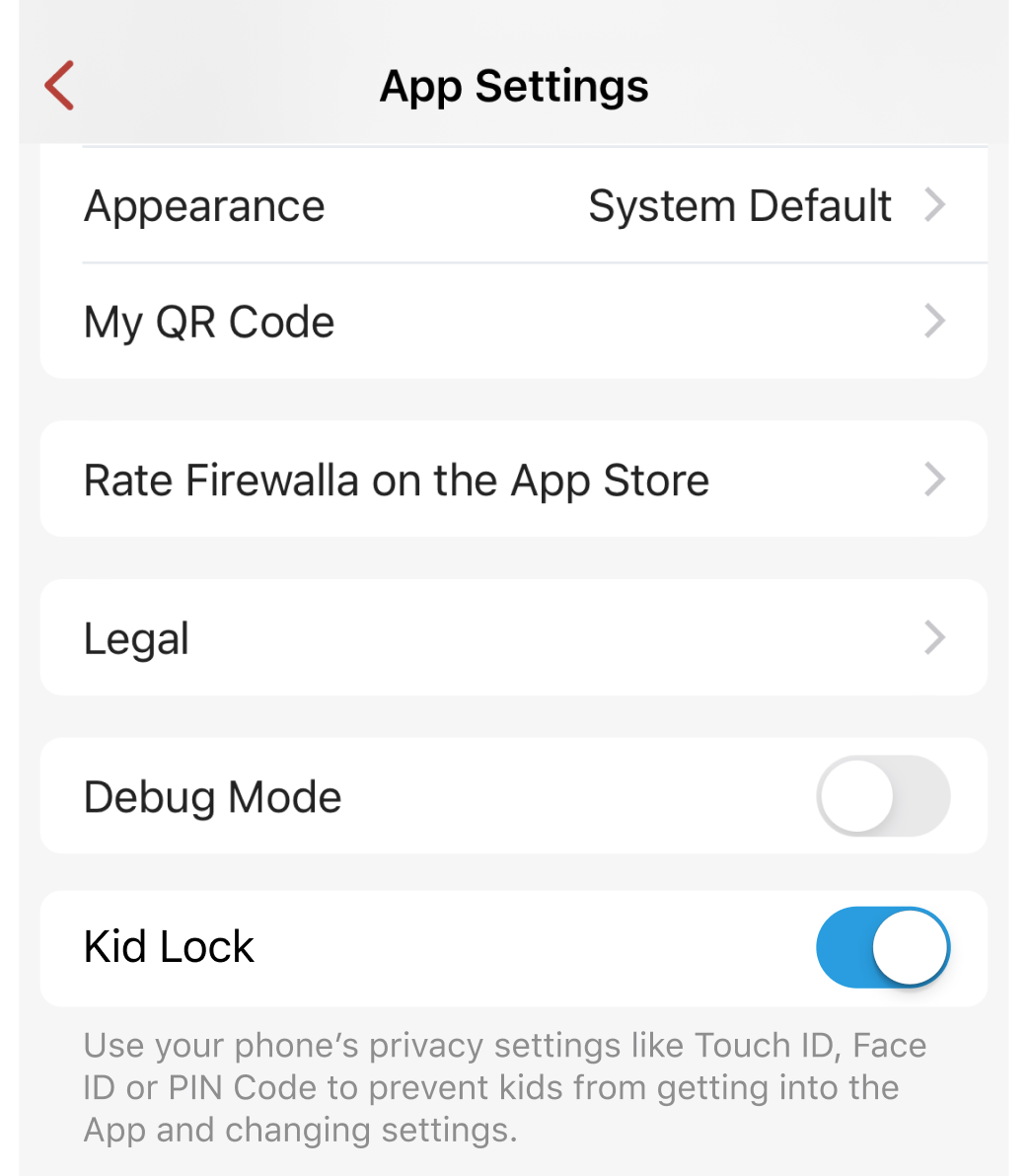
3. Kid Lock: Unlock App using Face ID, Touch ID, or PIN.
On App Settings -> turn on Kid Lock. Lock the app with Touch ID, Face ID, or PIN Code to prevent kids who share or have access to your device from getting into the Firewalla App and changing settings.
Learn more about Firewalla Parental Control.
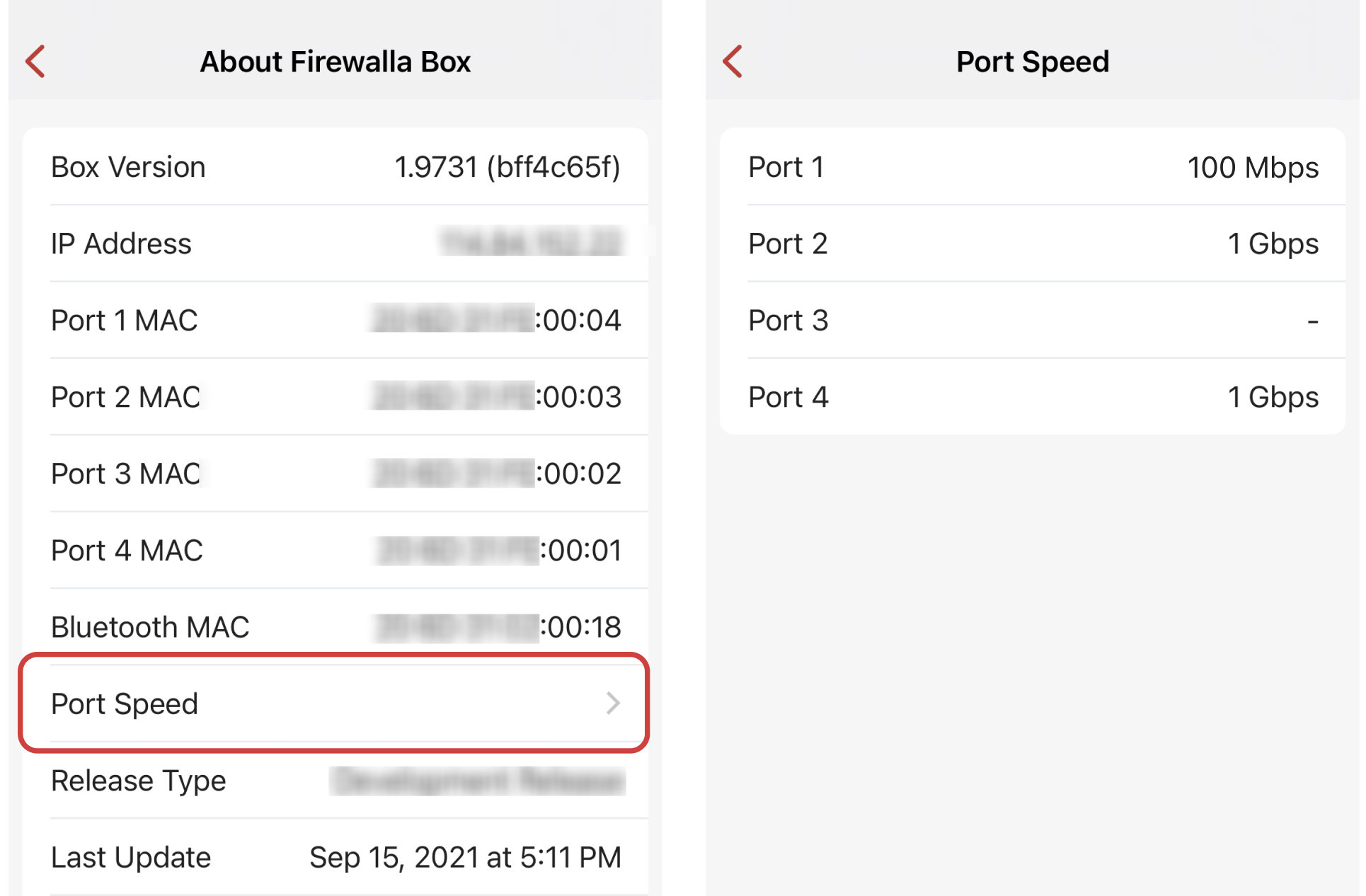
4. Ethernet Port Speed (1.973 only)
On Box Settings -> About -> Port Speed, you'll find the link speed of all the connected ports. If your Internet connection seems slow for any reason, you may check if your ethernet speed is capped at 100 Mbps or lower.
5. Directional Allow Rules
Firewalla is introducing directional ALLOW rules. The Direction for allow rules can be:
- Outbound only: This is now the default option. It allows traffic from your devices to the target, but not the other way around.
- Bi-directional: It will allow all traffic between the target and your local device. If a rule is set to bi-directional, others from the outside will be able to access your local devices. This may increase security risks, so if you are not sure about it, we recommend you use the default option.
Blocking rules are bi-directional unless specified in Targets.
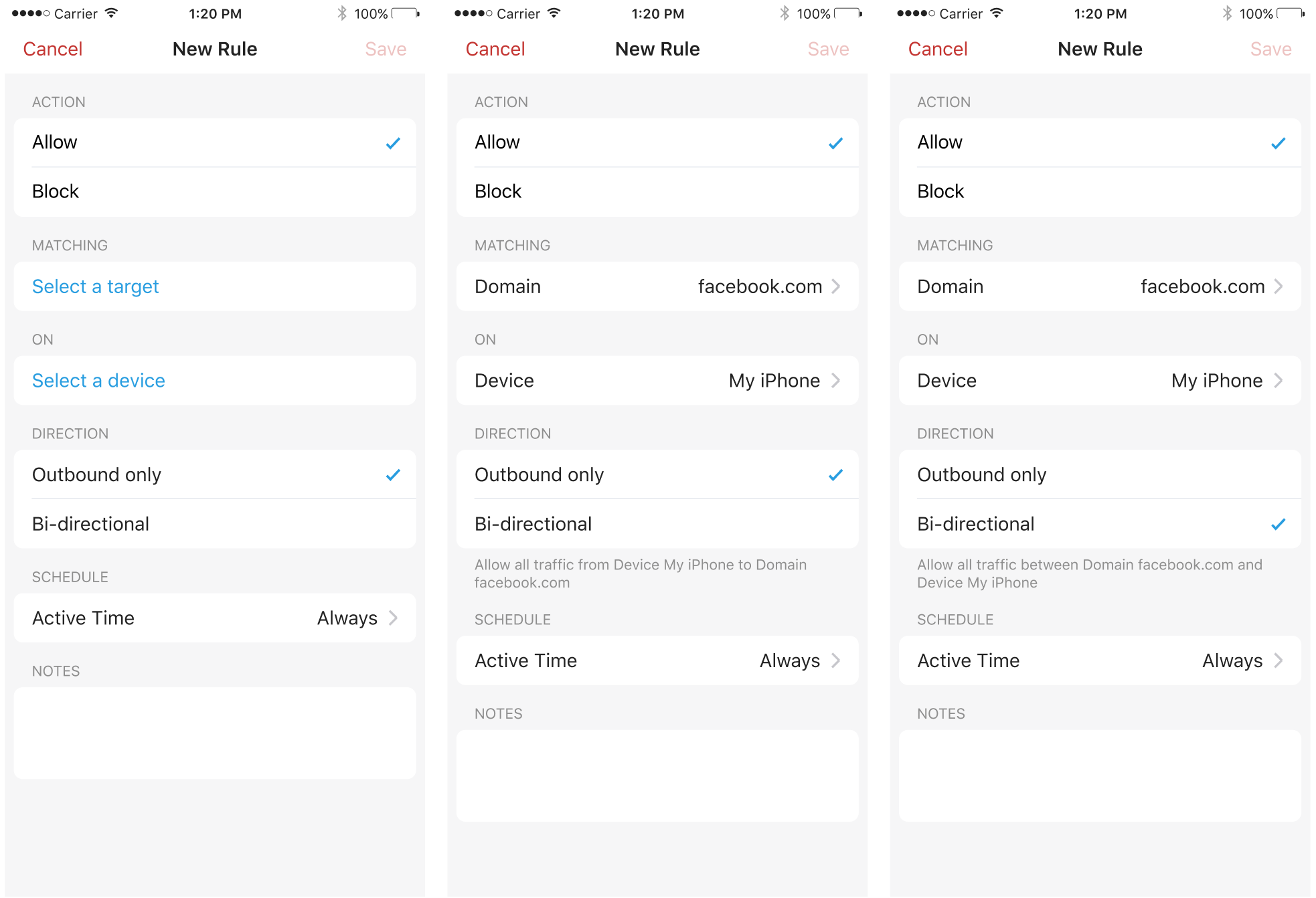
Note that existing rules were automatically converted to Bi-directional to match the old defaults and ensure continuity and nothing breaks with this migration. You may want to review and improve how your rules are set up given this new functionality.
6. Wi-Fi Management (Purple only)
Firewalla Purple has a built-in Wi-Fi interface. This interface will appear as two logical interfaces; one can be used as an AP (Access Point) for short-distance Wi-Fi, and the other can be used in WISP (Wireless Internet Service Provider) mode to connect to APs with the most commonly used Wi-Fi security protocols: WPA, WPA2 Personal, WPA2 Enterprise. WPA3 is not supported for now.
Learn more on Firewalla Purple: Short distance Wi-Fi
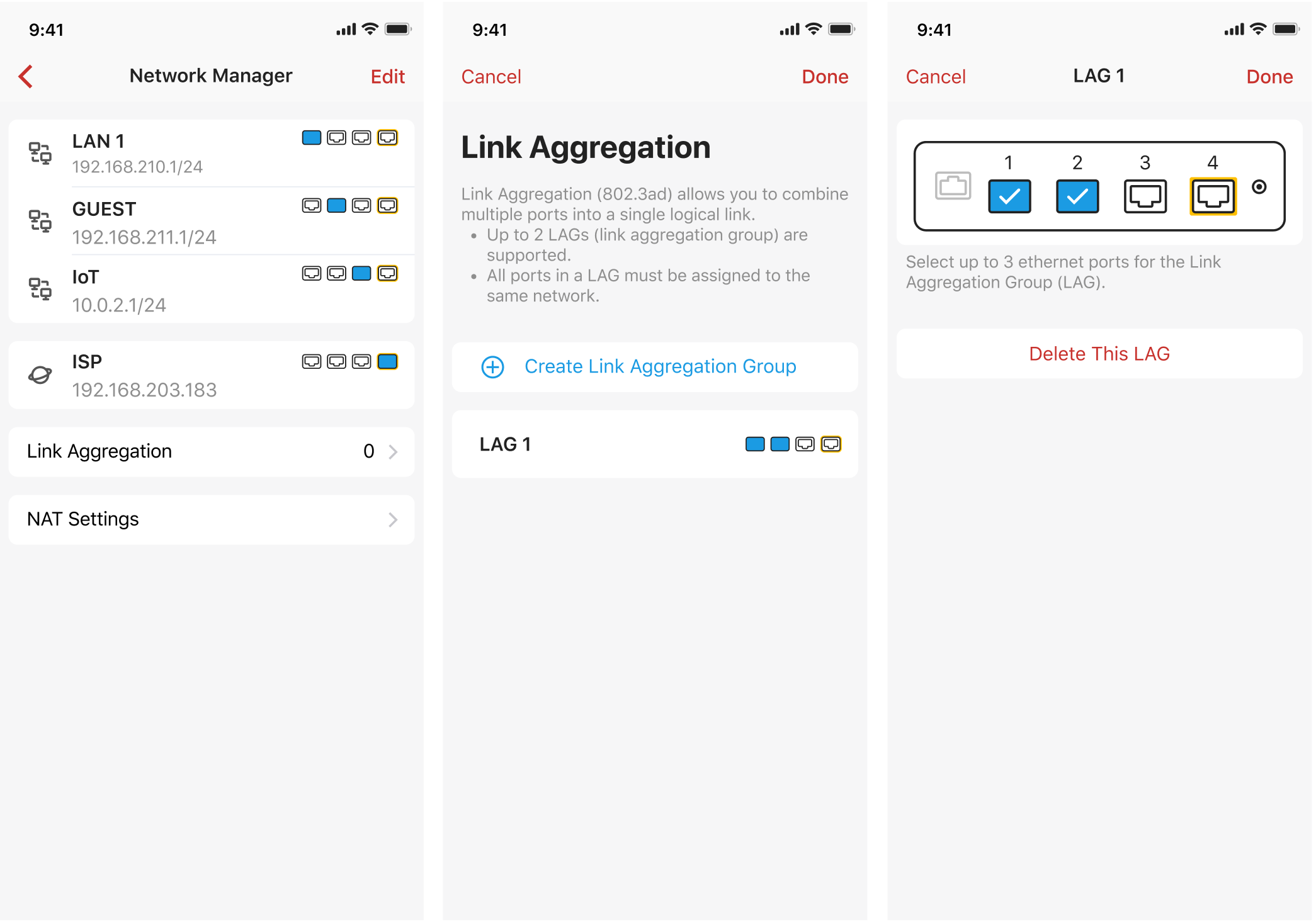
7. Link Aggregation (Gold only)
Link Aggregation is now supported on Firewalla Gold. For those of you who are eager to get network speeds over 1 Gbps, multiple ethernet ports can now be aggregated into one to provide you with a higher speed. For example, if you need 2 Gbps of bandwidth to transmit data, you can create a Link Aggregation Group (LAG) containing two of the gigabit ports on Firewalla Gold.
LAG can be used with LAN ports or WAN ports with a modem that supports link bonding.
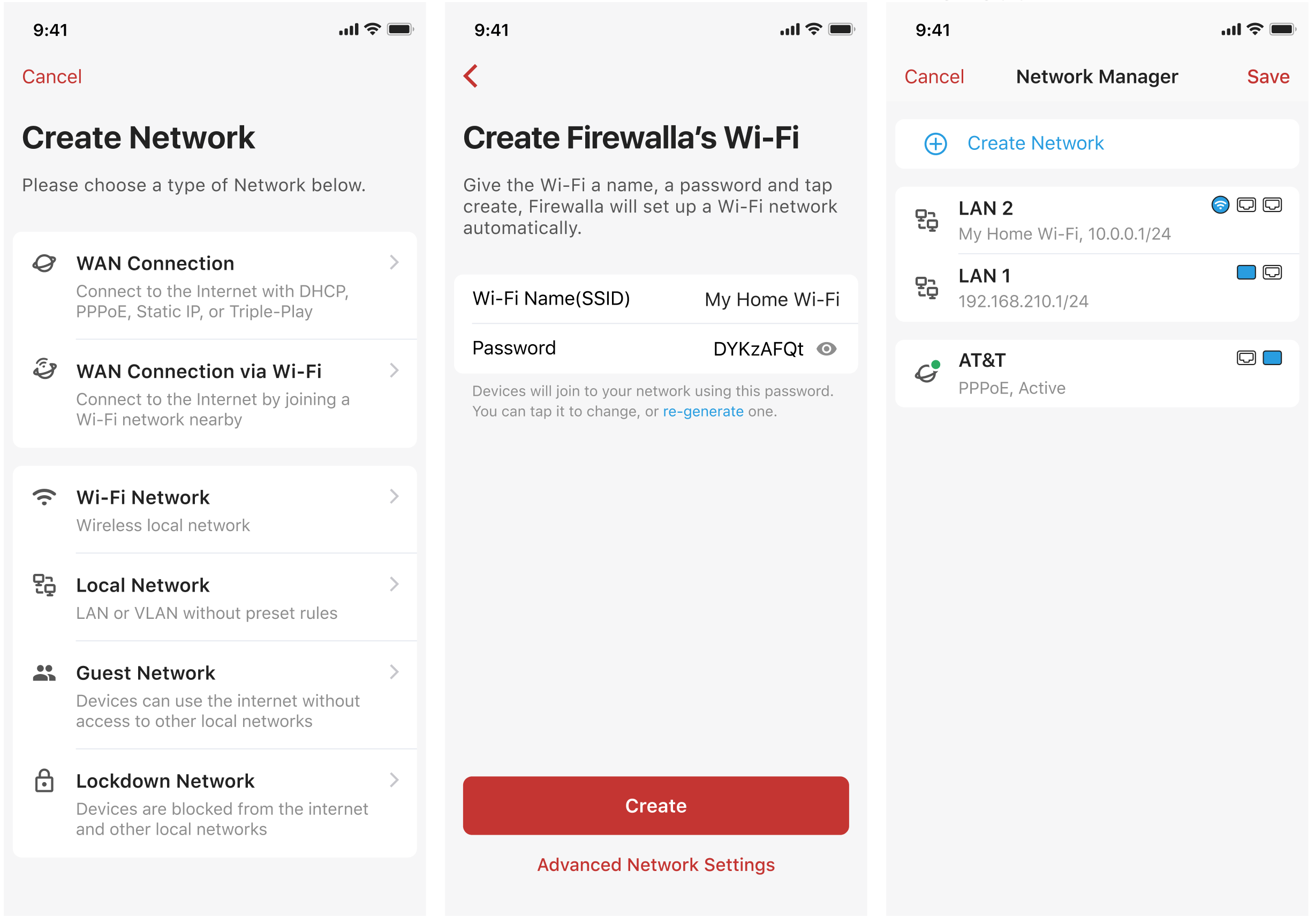
To create a LAG, under Network manager, tap Link Aggregation -> Create Link Aggregation Group.
- Up to three ports can be configured in a LAG. Up to two LAGs are supported.
- Static LAG configurations are not supported. LACP (802.3ad) only.
- For the box versions under 1.9731, VLANs are not supported on all LAGs.
Learn more on Link Aggregation
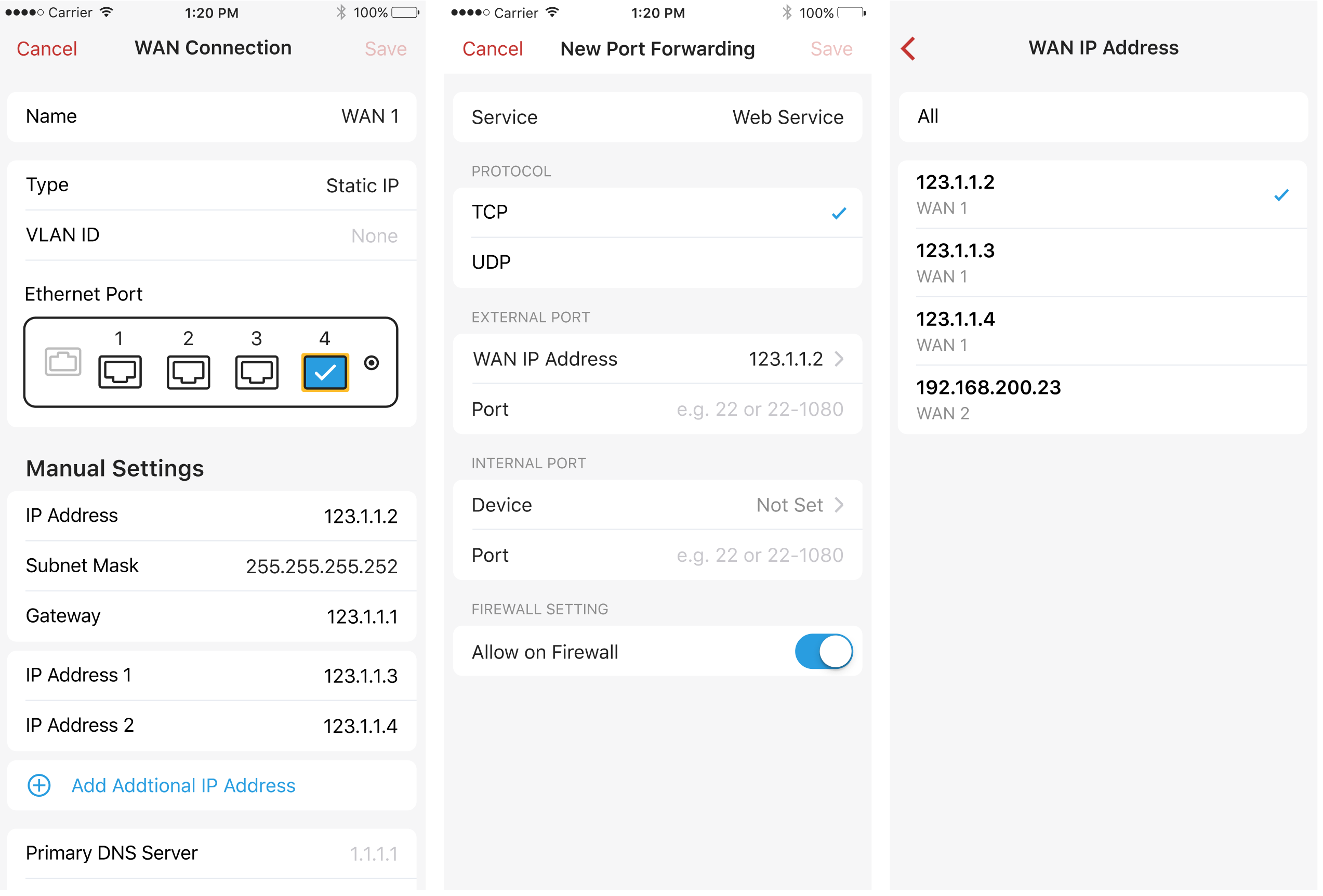
8. Multiple IP Addresses on WAN
For those of you who are given multiple static IP addresses by your ISP, Firewalla now supports configuring additional IP addresses on your WAN connection. By assigning multiple IPs on a single WAN, you can forward different ports to different IP addresses, and set DMZ host on any specific IP addresses.
For now, up to 5 additional IPs are supported on one WAN interface.
Learn more about Network Manager.
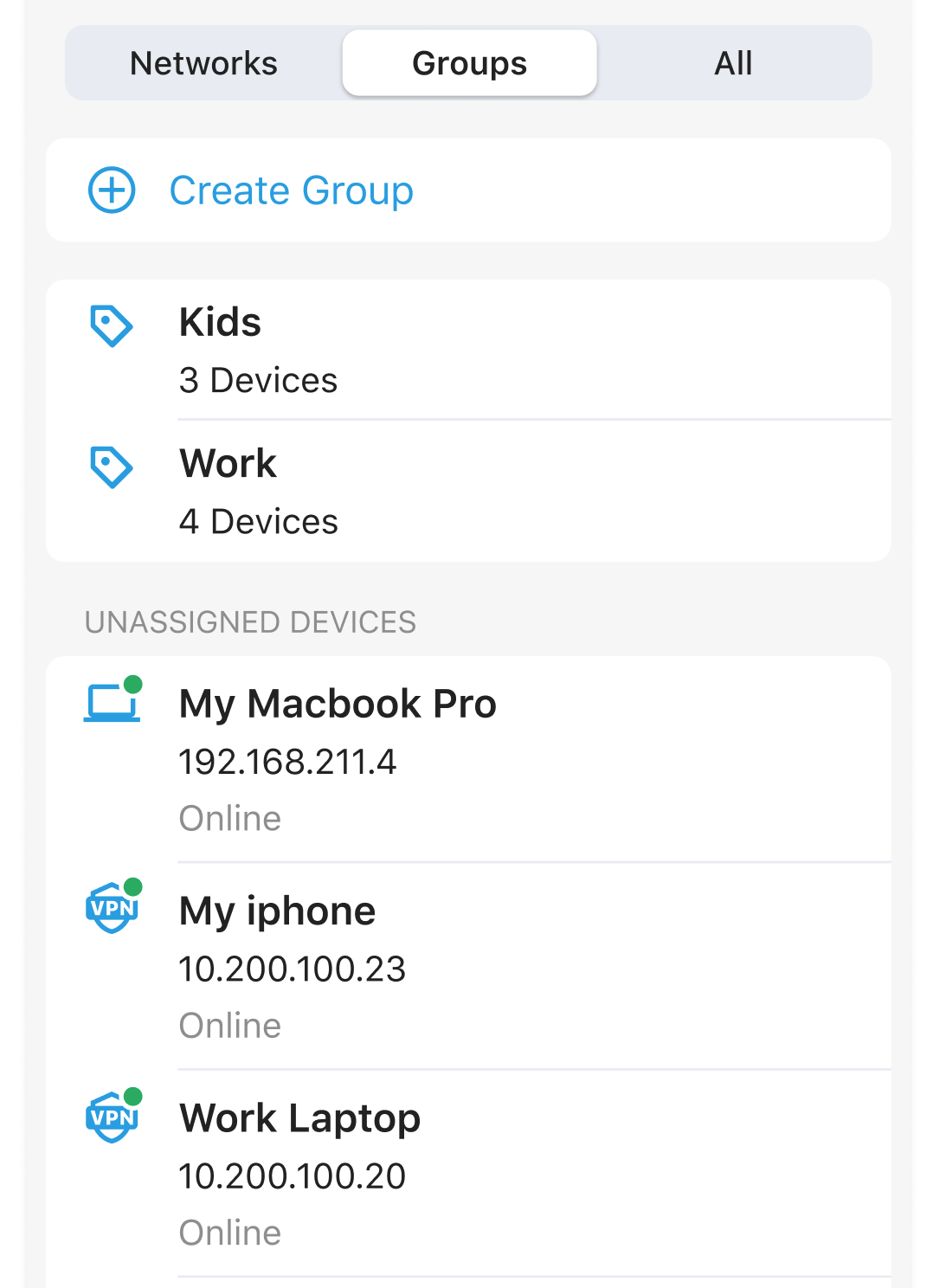
Enhancement:
1. New icon for devices connected via VPN (WireGuard only)
New icon to easily identify devices on the WireGuard VPN network.
Bug Fixes:
- Fixed the issue of showing incorrect direction for blocked flows
-
Fixed the Multi-WAN failover setting: Failback should be ON by default
- Fixed the issue of Block ICMP(Ping) is turned On by default in Bridge Mode
- Fixed several UI issues
Known Issue:
- On Android app, if you create a Link Aggregation Group and assign the LAG to one of your existing local networks, all the rules and IP reservations on the local network will be lost. This issue is already fixed on the latest android app release.

Comments
6 comments
The pace of development with this platform is incredible, you guys are doing a fantastic job!
Pause for Today means until Midnight?
Kid Lock: wasn't there already an option to secure the app? Was it simply renamed?
You must try really hard to get the interface to be the same between ios and android. I haven't used another app on android where I have to scroll up and down so much to select the time.
Directionality of rules is a move away from conntrack? Do Outbound-only rules leverage conntrack? So that return traffic is allowed, but not tcp/udp session setup.
Moving these to bidirectional, do you still expect to leverage conntrack, but in both directions?
Moving outbound rules to bi-directional sounds dangerous and could open up unexpected security holes.
Is there a packet flow diagram through the firewall/iptables? I don't need every detail regrading labels, but a simple 'day in the life of a packet' with the high-level blocks the traffic is moving through.
Adam,
Up until now, it appears that allow rules were always bi-directional. At least we have the option to make them unidirectional now.
https://help.firewalla.com/hc/en-us/community/posts/4406900595219-WARNING-Allow-rules-to-IP-or-Domain-are-BI-DIRECITONAL-
Thanks Chris. This makes sense. Unidirectional rules are s a good addition.
Also, of this is done via conntrack, which is may not be, it's not an issue.
The thread your linked implies it is not stateful and is stateless in both directions.
We really need an order of operations for how rules are processed and in what order. Or if a priority can be added or if there is implicit allow or deny by default.
It's not well documented, which may not be needed for most users. But advanced users will want to know this AND can help steer better decisions being made with real life use-cases, as long as they are not one-offs
Please sign in to leave a comment.