USN-5488-1: OpenSSL vulnerability - CRITICAL
There is a new OpenSSL vulnerability where OpenSSL could be made to crash or run programs when the c_rehash script is used.
When will you push a security patch for this.
ALSO, there are another 46 high and 93 medium severity vulnerabilities on the Gold. Could the available security patches be pushed to all devices as a priority?
Sources: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-2068, https://ubuntu.com/security/notices/USN-5488-1, https://ubuntu.com/security/CVE-2022-2068
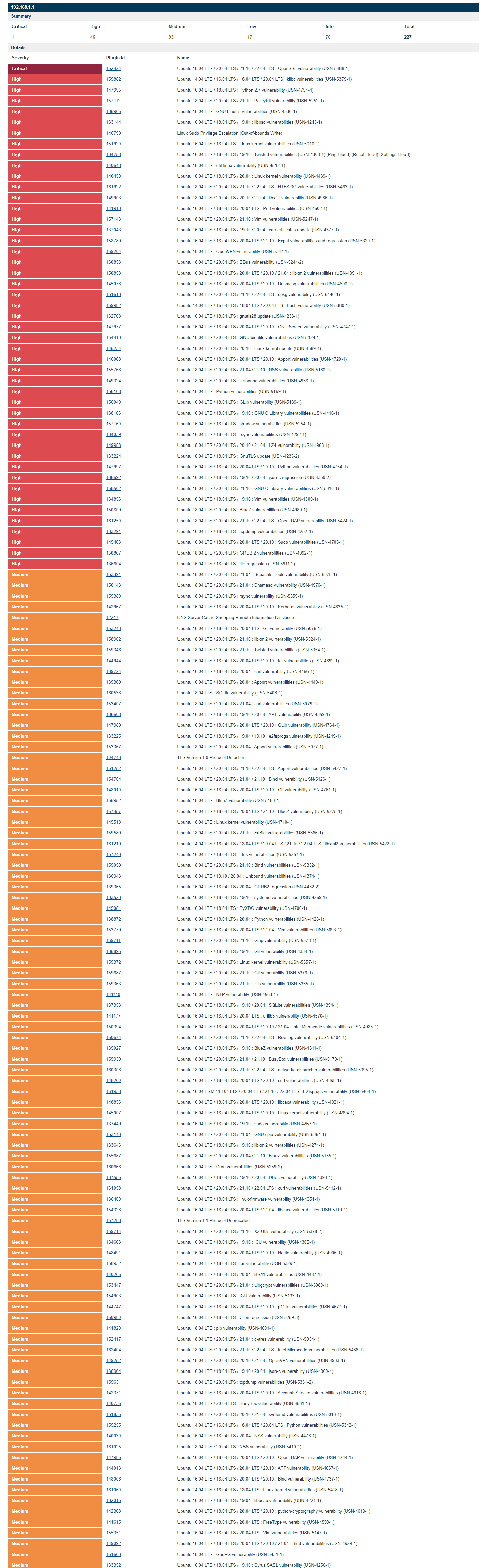
-
Thank you for the note.
First, we only patch vulnerabilities that are specific to running Firewalla. (We also actively monitor the impacted CVE's and patch them with each release) If you look above, things like "vim", really don't apply to us.
As for the OpenSSL CVE's, we do track them. The ones you listed are related to c_rehash, this is something we don't use. And even if we use it, the vulnerability is pretty much privilege escalation
On such operating systems, an attacker could execute arbitrary commands with the privileges of the script.
Due to the nature of how firewalla look at network packets, firewalla user "pi" has sudo access to the system already; so if you can get into the system, you are essentially root.
Please sign in to leave a comment.
Comments
1 comment