VLAN setup help
Hi everyone,
Had a (mostly) Omada network, and decided to upgrade my ER605 Omada router to the FWG. Setup went ok, not great. But now I'm really stuck on the VLAN setup. I went through and setup everything I believe correctly (clearly I'm missing something). When you join the IoT wireless network devices can't get an IP address. Additionally, when I hardwire something to port 3 of the FWG (setup for the VLAN), it's still showing with an IP of 192.168.10.x instead of the VLAN IP of 192.168.30.x. What am I missing?
Here's a config of my network:

On my old Omada routed network, I had multiple VLANS (parents, kids, IoT). On this new network especially with parental controls built in, I only see the need for an IoT network to keep those devices from accessing my laptop, etc. So just normal trusted main network, and 1 VLAN for IoT.
I setup the firewalla VLAN I believe correctly as seen here:
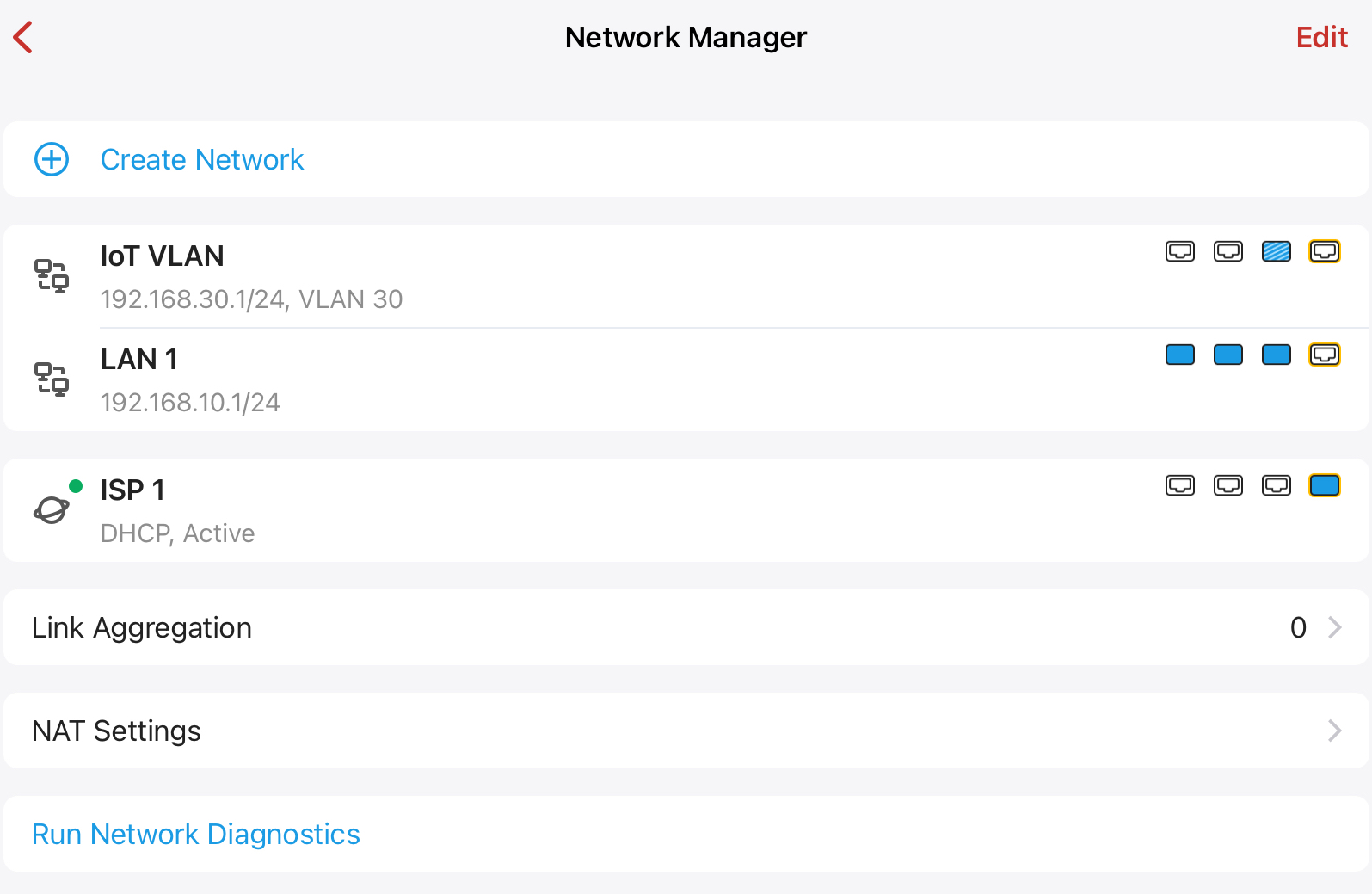

And here's what I've configured on the Omada controller:


-
Your Firewalla setup looks good to me, the only thing I've really noticed from your screenshots is that your network on the Omada isn't setup as a VLAN only and is set to a routing Interface, so perhaps its something to do with that part of the setup?
I will add however that I had no end of issues getting Firewalla and a Unifi setup running properly with (several) vLANs, and ended up blowing away the Firewalla setup and starting again from the ground up (ie in the Unifi interface) and working backwards to Firewalla until it eventually worked, no real reason why.
-
You're setting up two DHCP servers. You have DHCP Server on, on the Firewalla and on the Omada.
I use Omada for my AP only. I have my DHCP Server as my FWG+. My Switch is a NetGear switch (was free). I use port 3 from my FWG+ to port 24 on my NetGear switch. In the Switch I have to "Tag" port 24 to allow VLAN 300 (my guest network) and VLAN 900 (my IoT network). Tag as in allowing those VLANs to pass through that port. I then also have to take 3 other ports with the same VLANs (I have 3 TP-Link APs).
For the AP setup, it looks good. You set up the profile and "Tagged" that profile as your VLAN.
Port 3 is only "Tagged" on the Firewalla to allow that VLAN to travel through. Since you have your LAN across all 3 ports, that would be why you are not getting the correct IP address. If you created a completely separate LAN for your IoT vs a VLAN then it would work as you expect.
VLAN are "Virtual", it allows it to run on top of you main LAN network, so unless you plug in a device to port 3 that you can explicitly define a VLAN Trunk of 30, you will only get the Main LAN IP Address.
Since you have a unmanaged switch on port 3 of your firewalla, I don't think it can operate in VLAN mode. You will have to define a LAN for it. Then set up rules to allow/block. If you want WiFi IoT you would have to specify a different IP Subnet for the WiFi as a VLAN. Unless you get a Managed Switch to put in place on Port 3 of your Firewalla that you can "Tag" as allowing only that VLAN to pass through.
Please sign in to leave a comment.
Comments
2 comments